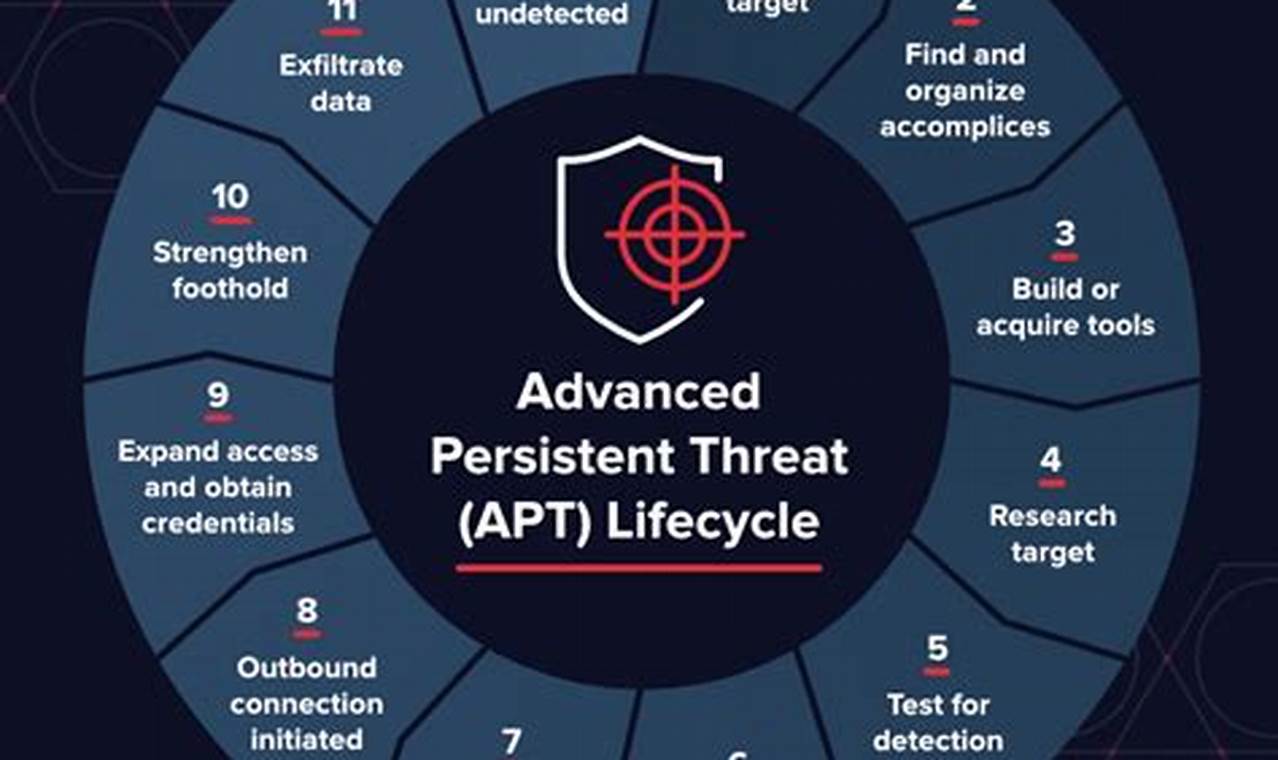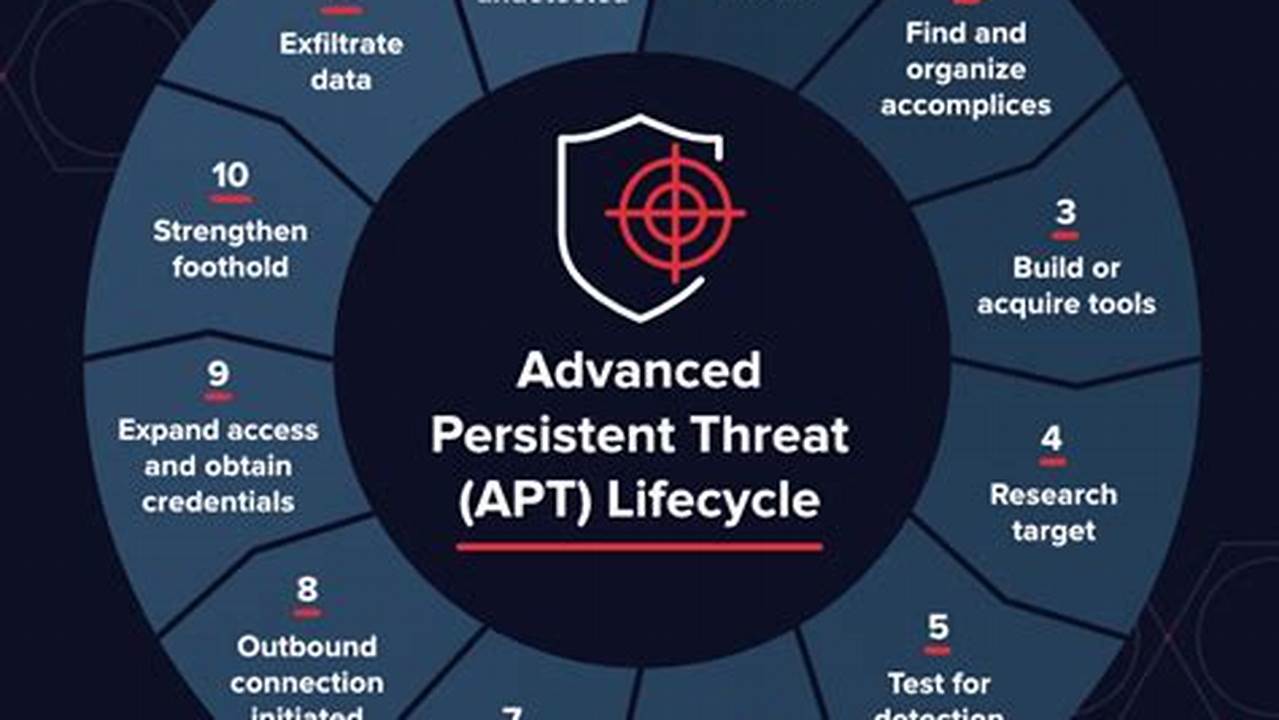
Advanced persistent threat (APT) detection involves identifying and responding to sophisticated cyberattacks that target specific organizations or individuals over an extended period. APTs are typically carried out by highly skilled attackers who employ stealthy techniques to evade detection and achieve their objectives, which can range from data theft to sabotage.
APT detection requires a multi-layered approach that combines technical solutions, such as intrusion detection systems and endpoint security, with human expertise and threat intelligence. By continuously monitoring networks and systems for suspicious activity, organizations can detect and respond to APTs before they cause significant damage.
Advanced persistent threat detection is crucial for protecting organizations from the increasing sophistication and frequency of cyberattacks. By implementing effective APT detection measures, organizations can strengthen their cybersecurity posture, reduce the risk of data breaches, and ensure the continuity of their operations.
Advanced persistent threat detection
Advanced persistent threat (APT) detection encompasses a wide range of activities and techniques aimed at identifying and responding to sophisticated cyberattacks. Understanding the different aspects of APT detection is crucial for organizations to effectively protect themselves from these threats.
- Monitoring: Continuous surveillance of networks and systems for suspicious activity
- Detection: Identifying and analyzing potential APT indicators, such as unusual network traffic or unauthorized access attempts
- Investigation: Thorough examination of detected threats to determine their scope and impact
- Response: Taking appropriate actions to contain, mitigate, and eradicate APT attacks
- Threat intelligence: Gathering and analyzing information about APT groups, their tactics, and their targets
- Collaboration: Sharing threat intelligence and best practices with other organizations and government agencies
- Education and awareness: Training employees to recognize and report suspicious activity
- Technology: Implementing and maintaining security technologies, such as intrusion detection systems and endpoint security solutions
These key aspects of APT detection are interconnected and interdependent. Effective APT detection requires a comprehensive and holistic approach that combines technical solutions, human expertise, and ongoing collaboration. By understanding and addressing these aspects, organizations can significantly improve their ability to detect and respond to advanced persistent threats.
Monitoring
Monitoring is a critical component of advanced persistent threat (APT) detection. By continuously surveilling networks and systems for suspicious activity, organizations can identify potential threats and take steps to mitigate them before they can cause significant damage.
APT attacks are often stealthy and sophisticated, making them difficult to detect. However, by monitoring for suspicious activity, organizations can identify patterns and anomalies that may indicate an APT attack is underway. For example, organizations may monitor for unusual network traffic, unauthorized access attempts, or changes to critical system files.
The importance of monitoring as a component of APT detection cannot be overstated. Without continuous monitoring, organizations would be far more vulnerable to APT attacks. By proactively monitoring their networks and systems, organizations can significantly improve their chances of detecting and responding to APT attacks before they can cause serious harm.
In practice, organizations can implement a variety of monitoring tools and techniques to detect suspicious activity. These may include intrusion detection systems (IDS), security information and event management (SIEM) systems, and endpoint security solutions. Organizations should also regularly review their security logs and monitor for any unusual activity.
By understanding the connection between monitoring and APT detection, organizations can take steps to improve their security posture and reduce their risk of being victimized by an APT attack.
Detection
Detection is a critical component of advanced persistent threat (APT) detection. APT attacks are often stealthy and sophisticated, making them difficult to detect. However, by identifying and analyzing potential APT indicators, organizations can identify potential threats and take steps to mitigate them before they can cause significant damage.
Potential APT indicators can include unusual network traffic, unauthorized access attempts, or changes to critical system files. By monitoring for these indicators, organizations can identify APT attacks at an early stage and take steps to contain them.
For example, if an organization detects unusual network traffic coming from an unknown source, it may be an indication of an APT attack. The organization can then investigate the traffic to determine if it is malicious and take steps to block it.
Detection is a complex and challenging task, but it is essential for protecting organizations from APT attacks. By understanding the importance of detection and implementing effective detection measures, organizations can significantly improve their security posture and reduce their risk of being victimized by an APT attack.
Investigation
Investigation is a critical component of advanced persistent threat (APT) detection. APT attacks are often stealthy and sophisticated, making them difficult to detect. Once an APT attack has been detected, it is important to conduct a thorough investigation to determine its scope and impact.
- Determining the extent of the attack: The first step in investigating an APT attack is to determine the extent of the attack. This includes identifying the systems that have been compromised, the data that has been stolen, and the impact on the organization’s operations.
- Understanding the attacker’s objectives: It is also important to understand the attacker’s objectives. This can help organizations to prioritize their response and take steps to mitigate the impact of the attack.
- Identifying the attacker’s methods: Understanding the attacker’s methods can help organizations to improve their security posture and prevent future attacks.
- Preserving evidence: It is important to preserve evidence of the attack for forensic analysis. This evidence can help to identify the attacker and bring them to justice.
Investigation is a complex and challenging task, but it is essential for protecting organizations from APT attacks. By conducting a thorough investigation, organizations can determine the scope and impact of an APT attack, and take steps to mitigate the damage and prevent future attacks.
Response
Response is a critical component of advanced persistent threat (APT) detection. APT attacks are often stealthy and sophisticated, making them difficult to detect and contain. Once an APT attack has been detected, it is important to take immediate action to contain the attack, mitigate its impact, and eradicate the threat.
Containment measures can include isolating infected systems, blocking network access, and restricting user privileges. Mitigation measures can include restoring compromised data, patching vulnerabilities, and implementing additional security controls. Eradication measures can include removing malware, identifying and neutralizing attacker infrastructure, and hunting for any remaining traces of the attack.
A timely and effective response to an APT attack can significantly reduce the damage caused by the attack and help to prevent future attacks. By understanding the importance of response and implementing effective response measures, organizations can improve their security posture and reduce their risk of being victimized by an APT attack.
Threat intelligence
Threat intelligence is a critical component of advanced persistent threat (APT) detection. APT attacks are often stealthy and sophisticated, making them difficult to detect and contain. Threat intelligence can help organizations to identify potential APT attacks, understand the attacker’s objectives and methods, and take steps to mitigate the impact of an attack.
There are a number of different sources of threat intelligence, including open-source intelligence, commercial threat intelligence providers, and government agencies. Organizations can also collect their own threat intelligence by monitoring their networks and systems for suspicious activity.
Threat intelligence is used to inform a variety of security decisions, including:
- Identifying potential APT attacks
- Understanding the attacker’s objectives and methods
- Developing strategies
- Mitigating the impact of an APT attack
By understanding the connection between threat intelligence and APT detection, organizations can improve their security posture and reduce their risk of being victimized by an APT attack.
Collaboration
Collaboration is an essential component of advanced persistent threat (APT) detection. APT attacks are often stealthy and sophisticated, making them difficult to detect and contain. By sharing threat intelligence and best practices with other organizations and government agencies, organizations can improve their ability to detect and respond to APT attacks.
There are a number of different ways that organizations can collaborate on APT detection. One common method is to join a threat intelligence sharing community. These communities allow organizations to share information about APT attacks, including their tactics, techniques, and procedures (TTPs). This information can help organizations to identify potential APT attacks, understand the attacker’s objectives and methods, and develop strategies to mitigate the impact of an attack.
Another way that organizations can collaborate on APT detection is to participate in joint investigations. Joint investigations allow organizations to pool their resources and expertise to investigate APT attacks. This can help to identify the attacker, understand the scope of the attack, and develop strategies to mitigate the impact of the attack.
By collaborating with other organizations and government agencies, organizations can improve their ability to detect and respond to APT attacks. Collaboration can help organizations to identify potential APT attacks, understand the attacker’s objectives and methods, and develop strategies to mitigate the impact of an attack.
Education and awareness
In the realm of advanced persistent threat (APT) detection, educating and raising awareness among employees plays a pivotal role in strengthening an organization’s defenses. Employees are often the first line of defense against APT attacks, as they may encounter suspicious activity or anomalies in their daily work. By training employees to recognize and report such activities, organizations can significantly improve their ability to detect and respond to APT attacks.
- Identifying Phishing Emails: Phishing emails are a common method used by APT attackers to gain access to sensitive information or infect systems with malware. Educating employees on how to identify phishing emails, such as those with suspicious links or attachments, empowers them to avoid falling victim to these attacks.
- Monitoring Unusual Network Activity: Employees who are aware of the organization’s normal network activity patterns can be valuable in detecting anomalies that may indicate an APT attack. Training them to monitor for unusual network traffic, such as sudden spikes in bandwidth usage or connections from unfamiliar IP addresses, can help organizations identify potential threats early on.
- Reporting Suspicious Behavior: Encouraging employees to report any suspicious behavior or activities they observe is crucial. This may include observing unknown individuals taking photographs of restricted areas, attempts to access unauthorized data, or unusual interactions with physical security systems. By creating a culture of vigilance and reporting, organizations can increase the likelihood of detecting APT attacks before they escalate.
- Understanding Social Engineering Techniques: APT attackers often employ social engineering techniques to manipulate employees into divulging sensitive information or taking actions that compromise security. Educating employees on these techniques, such as pretexting, impersonation, and baiting, can help them resist these attacks and protect the organization’s assets.
By implementing comprehensive education and awareness programs, organizations can equip their employees with the knowledge and skills to recognize and report suspicious activity. This, in turn, strengthens the organization’s overall APT detection capabilities and reduces the risk of successful attacks.
Technology
In the modern threat landscape, technology plays a pivotal role in advanced persistent threat (APT) detection. Implementing and maintaining robust security technologies are essential components of a comprehensive APT detection strategy.
- Intrusion Detection Systems (IDS): IDS monitors network traffic for suspicious activities that may indicate an APT attack. By analyzing patterns and detecting anomalies, IDS can alert organizations to potential threats in real-time.
- Endpoint Security Solutions: Endpoint security solutions protect individual devices, such as laptops and servers, from unauthorized access, malware infections, and other threats. They provide layered protection, including antivirus, anti-malware, and intrusion prevention capabilities.
- Security Information and Event Management (SIEM): SIEM collects and analyzes security logs from various sources, including IDS and endpoint security solutions. It provides a centralized view of security events, enabling organizations to detect and respond to threats more efficiently.
- Network Segmentation: Network segmentation divides the network into smaller, isolated segments, limiting the spread of an APT attack. By isolating critical systems and data, organizations can minimize the potential impact of a breach.
These security technologies work together to create a multi-layered defense system that enhances APT detection capabilities. By implementing and maintaining these technologies, organizations can strengthen their security posture, reduce the risk of successful APT attacks, and protect their valuable assets.
Advanced Persistent Threat Detection
Advanced persistent threat (APT) detection is a critical aspect of cybersecurity, safeguarding organizations from sophisticated and targeted cyberattacks. Here are answers to some frequently asked questions about APT detection:
Question 1: What is the difference between APT detection and traditional threat detection?
Traditional threat detection focuses on identifying and blocking known threats, such as viruses and malware, based on predefined signatures. APT detection, on the other hand, aims to uncover stealthy and persistent attacks that often evade traditional detection methods. It involves analyzing large volumes of data, detecting anomalies, and identifying patterns that may indicate an APT attack.
Question 2: How can organizations improve their APT detection capabilities?
Organizations can enhance their APT detection capabilities by implementing a multi-layered defense strategy that includes:
- Deploying advanced security technologies, such as intrusion detection systems (IDS) and endpoint security solutions
- Continuously monitoring network traffic and system activities for suspicious behavior
- Conducting regular security audits and vulnerability assessments
- Educating employees on security best practices and raising awareness about APT threats
Question 3: What are the common techniques used by APT attackers?
APT attackers employ various techniques to evade detection and achieve their objectives. These techniques include:
- Spear phishing and social engineering to gain access to sensitive information
- Exploiting zero-day vulnerabilities and using custom malware
- Moving laterally within the network to gain access to critical systems
- Exfiltrating data and intellectual property over extended periods
Question 4: How can organizations respond effectively to an APT attack?
Responding to an APT attack requires a comprehensive incident response plan. Organizations should:
Question 5: What is the role of threat intelligence in APT detection?
Threat intelligence plays a vital role in APT detection by providing organizations with up-to-date information about known APT groups, their tactics, techniques, and procedures (TTPs). This knowledge enables organizations to strengthen their defenses, prioritize threat mitigation efforts, and stay ahead of potential attacks.
Question 6: How can organizations measure the effectiveness of their APT detection capabilities?
Measuring the effectiveness of APT detection capabilities is critical for continuous improvement. Organizations can evaluate their effectiveness by:
- Tracking key performance indicators (KPIs), such as the number of detected APT attacks and the time taken to respond
- Conducting regular security assessments and threat hunting exercises
- Analyzing the results of security audits and incident response drills
By addressing these frequently asked questions, organizations gain a deeper understanding of APT detection, its importance, and the steps they can take to strengthen their defenses against these sophisticated threats.
Transition to the next article section: Advanced Persistent Threat Detection: Best Practices
Advanced Persistent Threat Detection Tips
Advanced persistent threats (APTs) pose significant risks to organizations, requiring proactive detection measures. Here are several crucial tips to enhance APT detection capabilities:
Tip 1: Implement a Layered Defense Strategy
Deploy a combination of security technologies, including intrusion detection systems (IDS), endpoint security solutions, and network segmentation, to create a multi-layered defense against APTs.
Tip 2: Monitor Network Traffic and System Activities
Continuously monitor network traffic and system activities for suspicious behavior. Utilize security information and event management (SIEM) systems to centralize and analyze security logs for potential APT indicators.
Tip 3: Conduct Regular Security Audits and Vulnerability Assessments
Regularly conduct security audits and vulnerability assessments to identify potential weaknesses that APT attackers may exploit. Address vulnerabilities promptly to reduce the risk of successful attacks.
Tip 4: Educate Employees on Security Best Practices
Educate employees on security best practices and raise awareness about APT threats. Train them to recognize phishing attempts, avoid clicking on suspicious links, and report any unusual activities.
Tip 5: Utilize Threat Intelligence
Leverage threat intelligence feeds to stay informed about the latest APT groups, their tactics, and their targets. Use this information to enhance detection capabilities and prioritize threat mitigation efforts.
Tip 6: Measure the Effectiveness of Detection Capabilities
Regularly measure the effectiveness of APT detection capabilities by tracking key performance indicators (KPIs), conducting security assessments, and analyzing the results of incident response drills.
Tip 7: Implement an Incident Response Plan
Develop and implement a comprehensive incident response plan that outlines the steps to take in the event of an APT attack. This plan should include procedures for containment, eradication, and recovery.
Tip 8: Collaborate with External Partners
Collaborate with external partners, such as cybersecurity vendors and law enforcement agencies, to share threat intelligence and best practices. This collaboration can enhance detection capabilities and provide access to specialized expertise.
By implementing these tips, organizations can significantly enhance their ability to detect and respond to advanced persistent threats, safeguarding their valuable assets and protecting against cyberattacks.
Transition to the article’s conclusion: Advanced Persistent Threat Detection: Conclusion
Advanced Persistent Threat Detection
Advanced persistent threat (APT) detection is a critical component of a comprehensive cybersecurity strategy. By understanding the nature of APTs, implementing effective detection measures, and continuously monitoring and improving detection capabilities, organizations can significantly reduce their risk of falling victim to these sophisticated cyberattacks.
The exploration in this article has highlighted the importance of a multi-layered defense strategy, the role of threat intelligence, and the need for continuous vigilance and collaboration. Organizations must recognize that APT detection is an ongoing process that requires constant adaptation to the evolving threat landscape.
In conclusion, advanced persistent threat detection is essential for protecting organizations from the damaging effects of cyberattacks. By embracing the best practices outlined in this article, organizations can enhance their security posture, safeguard their valuable assets, and maintain their competitive edge in an increasingly digital world.
Youtube Video: