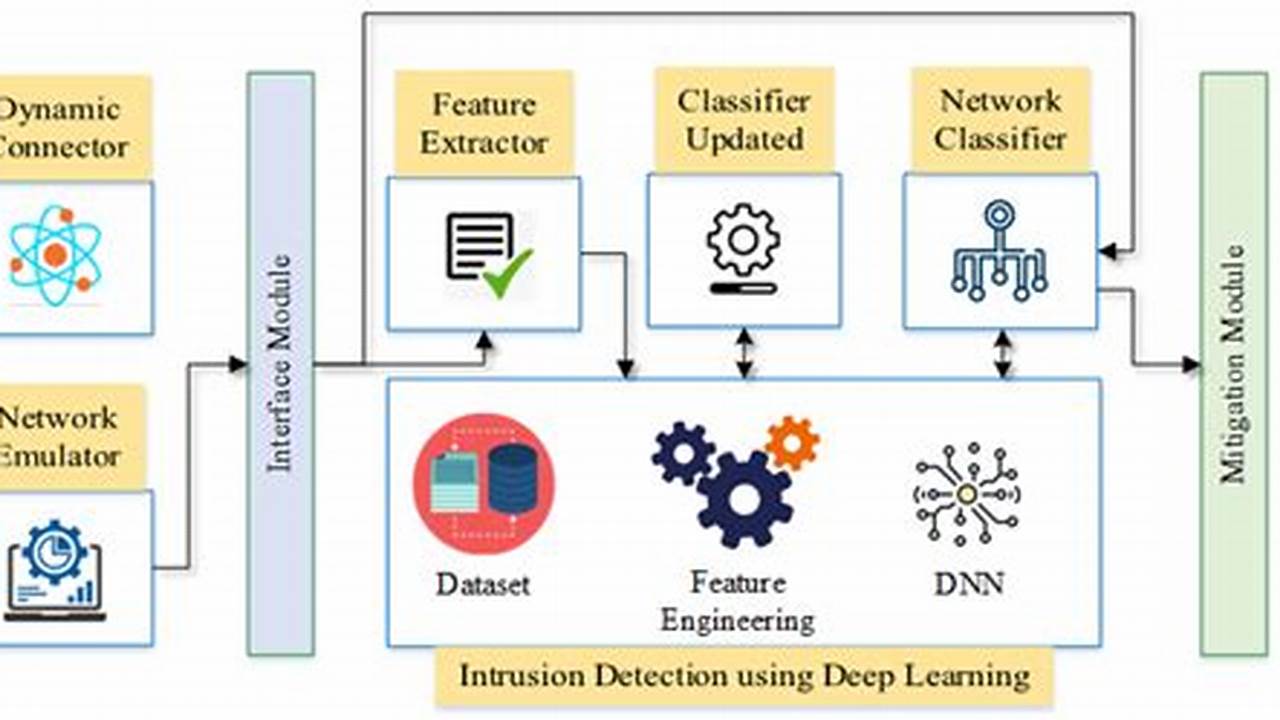
Attack detection is the process of identifying and responding to malicious activity on a computer system or network. It is a critical component of cybersecurity, as it can help organizations to protect their data and systems from unauthorized access, theft, or damage.
Attack detection systems typically use a variety of techniques to identify malicious activity. These techniques can include signature-based detection, anomaly-based detection, and heuristic-based detection. Signature-based detection identifies malicious activity by matching it to known patterns of attack. Anomaly-based detection identifies malicious activity by detecting deviations from normal patterns of behavior. Heuristic-based detection identifies malicious activity by using a set of rules or heuristics to identify suspicious activity.
Attack detection systems are an important part of any cybersecurity strategy. They can help organizations to identify and respond to malicious activity quickly and effectively, reducing the risk of damage to their data and systems.
Attack detection
Attack detection is a critical component of cybersecurity, as it can help organizations to protect their data and systems from unauthorized access, theft, or damage.
- Techniques: Signature-based, anomaly-based, heuristic-based
- Importance: Protects data and systems from malicious activity
- Benefits: Quick and effective response to attacks
- Challenges: Evolving attack methods, false positives
- Trends: Machine learning, artificial intelligence
- Tools: Security information and event management (SIEM) systems, intrusion detection systems (IDS)
- Best practices: Regularly update software, use strong passwords, implement security policies
These key aspects of attack detection are essential for organizations to understand in order to protect their data and systems from malicious activity. By implementing effective attack detection measures, organizations can reduce the risk of damage to their data and systems, and ensure the confidentiality, integrity, and availability of their information assets.
Techniques
Attack detection techniques are essential for identifying malicious activity on computer systems and networks. These techniques can be categorized into three main types: signature-based, anomaly-based, and heuristic-based.
- Signature-based detection identifies malicious activity by matching it to known patterns of attack. This technique is effective against known attacks, but it can be ineffective against new or unknown attacks.
- Anomaly-based detection identifies malicious activity by detecting deviations from normal patterns of behavior. This technique is effective against new or unknown attacks, but it can be prone to false positives.
- Heuristic-based detection identifies malicious activity by using a set of rules or heuristics to identify suspicious activity. This technique is effective against a wide range of attacks, but it can be complex to develop and maintain.
The choice of attack detection technique depends on a number of factors, including the type of system being protected, the level of security required, and the resources available. Organizations should use a combination of techniques to achieve the best possible protection against malicious activity.
Importance
Attack detection plays a vital role in protecting data and systems from malicious activity by identifying and responding to threats in a timely manner. Without effective attack detection, organizations would be vulnerable to a wide range of cyberattacks, including data breaches, ransomware attacks, and denial-of-service attacks.
-
Data Breaches
Attack detection can help to prevent data breaches by identifying and blocking unauthorized access to sensitive data. For example, an attack detection system might identify suspicious activity, such as an attempt to access a database without proper authorization, and block the attempt before any data can be stolen.
-
Ransomware Attacks
Attack detection can help to prevent ransomware attacks by identifying and blocking malicious software that encrypts data and demands a ransom payment. For example, an attack detection system might identify a suspicious file that is attempting to encrypt data and block the file before it can do any damage.
-
Denial-of-Service Attacks
Attack detection can help to prevent denial-of-service attacks by identifying and blocking malicious traffic that is designed to overwhelm a system and make it unavailable to legitimate users. For example, an attack detection system might identify a suspicious pattern of traffic that is attempting to flood a website with requests and block the traffic before it can cause any damage.
In addition to these specific examples, attack detection can also help to protect data and systems from a wide range of other malicious activities, including phishing attacks, malware attacks, and insider threats. By identifying and responding to threats in a timely manner, attack detection can help organizations to protect their data and systems from damage and disruption.
Benefits
Attack detection provides several benefits to organizations, including the ability to respond to attacks quickly and effectively. By identifying and responding to attacks in a timely manner, organizations can minimize the damage caused by the attack and reduce the risk of data loss or disruption of operations.
For example, if an attack detection system identifies a phishing attack, the organization can quickly take steps to block the attack and prevent any users from falling victim to the attack. Similarly, if an attack detection system identifies a ransomware attack, the organization can quickly take steps to isolate the infected systems and prevent the ransomware from spreading to other systems.
In addition to reducing the damage caused by attacks, a quick and effective response can also help organizations to maintain their reputation and customer trust. By demonstrating that they are taking proactive steps to protect their data and systems, organizations can reassure their customers that their information is safe and secure.
Challenges
Attack detection systems face a number of challenges, including the evolving nature of attack methods and the potential for false positives.
-
Evolving attack methods
Attackers are constantly developing new and more sophisticated ways to attack computer systems and networks. This means that attack detection systems must be constantly updated to keep up with the latest threats. However, it can be difficult to detect new attacks that are not yet known to the security community.
-
False positives
Attack detection systems can sometimes generate false positives, which are alerts that are triggered by legitimate activity. This can lead to unnecessary investigations and wasted resources. False positives can also be a nuisance to users, who may become desensitized to alerts and ignore real attacks.
Despite these challenges, attack detection systems are an essential part of any cybersecurity strategy. By identifying and responding to attacks quickly and effectively, organizations can minimize the damage caused by attacks and reduce the risk of data loss or disruption of operations.
Trends
Machine learning and artificial intelligence (AI) are playing an increasingly important role in attack detection. These technologies can be used to identify and respond to attacks more quickly and effectively than traditional methods.
One of the main advantages of using machine learning and AI for attack detection is that these technologies can be trained to identify new and unknown attacks. This is important because attackers are constantly developing new ways to attack computer systems and networks. Traditional attack detection methods, which rely on signatures or known patterns of attack, can be ineffective against new attacks.
Machine learning and AI can also be used to improve the accuracy of attack detection. Traditional attack detection methods can sometimes generate false positives, which are alerts that are triggered by legitimate activity. This can lead to unnecessary investigations and wasted resources. Machine learning and AI can be used to reduce the number of false positives by learning to distinguish between normal and malicious activity.
There are a number of real-life examples of how machine learning and AI are being used to improve attack detection. For example, Google uses machine learning to detect and block phishing attacks on its Gmail service. Microsoft uses AI to detect and respond to attacks on its Azure cloud platform. And Amazon Web Services (AWS) uses machine learning to detect and block DDoS attacks on its cloud platform.
The use of machine learning and AI for attack detection is a growing trend. These technologies have the potential to significantly improve the security of computer systems and networks.
Tools
Security information and event management (SIEM) systems and intrusion detection systems (IDS) are essential tools for attack detection. SIEM systems collect and analyze security logs from a variety of sources, including network devices, servers, and applications. IDS systems monitor network traffic for suspicious activity. Together, these tools can provide organizations with a comprehensive view of their security posture and help them to identify and respond to attacks quickly and effectively.
SIEM systems are typically used to collect and analyze security logs from a variety of sources, including network devices, servers, and applications. This data can be used to identify trends and patterns that may indicate an attack. For example, a SIEM system might identify a sudden increase in failed login attempts, which could indicate that an attacker is trying to brute force their way into a system.
IDS systems are typically used to monitor network traffic for suspicious activity. This data can be used to identify attacks in real time. For example, an IDS system might identify a packet that is attempting to exploit a known vulnerability in a web server. IDS systems can also be used to detect and block malicious traffic, such as phishing emails and malware.
SIEM and IDS systems are essential tools for attack detection. By collecting and analyzing security logs and network traffic, these tools can help organizations to identify and respond to attacks quickly and effectively. In addition, SIEM and IDS systems can be used to generate reports and alerts, which can help organizations to track their security posture and identify trends.
Best practices
Best practices such as regularly updating software, using strong passwords, and implementing security policies are essential components of attack detection. By following these best practices, organizations can reduce the risk of successful attacks and make it more difficult for attackers to compromise their systems. Regularly updating software patches security vulnerabilities that could be exploited by attackers. Using strong passwords makes it more difficult for attackers to guess or crack passwords and gain access to systems. Implementing security policies helps to define and enforce security measures within an organization, ensuring that all employees are aware of and follow security best practices.
For example, the 2017 Equifax data breach was caused by the company’s failure to patch a known vulnerability in its software. The attackers were able to exploit this vulnerability to gain access to the company’s systems and steal the personal data of millions of customers. This breach could have been prevented if Equifax had followed the best practice of regularly updating its software.
Best practices for attack detection are essential for protecting organizations from cyberattacks. By following these best practices, organizations can reduce the risk of successful attacks and protect their data and systems.
Attack Detection FAQs
Attack detection is a critical component of cybersecurity, as it can help organizations to protect their data and systems from unauthorized access, theft, or damage. Here are some frequently asked questions about attack detection:
Question 1: What is attack detection?
Answer: Attack detection is the process of identifying and responding to malicious activity on a computer system or network.
Question 2: Why is attack detection important?
Answer: Attack detection is important because it can help organizations to protect their data and systems from unauthorized access, theft, or damage.
Question 3: What are the different types of attack detection techniques?
Answer: The three main types of attack detection techniques are signature-based, anomaly-based, and heuristic-based.
Question 4: What are the challenges of attack detection?
Answer: The main challenges of attack detection are the evolving nature of attack methods and the potential for false positives.
Question 5: What are the best practices for attack detection?
Answer: The best practices for attack detection are regularly updating software, using strong passwords, and implementing security policies.
Question 6: What are the future trends in attack detection?
Answer: The future trends in attack detection include the use of machine learning and artificial intelligence.
Attack detection is a complex and challenging field, but it is essential for protecting organizations from cyberattacks. By understanding the different types of attack detection techniques, the challenges of attack detection, and the best practices for attack detection, organizations can improve their security posture and protect their data and systems from unauthorized access, theft, or damage.
Attack detection is an ongoing process, and organizations should regularly review their security measures and update their attack detection systems to keep up with the latest threats.
Attack Detection Tips
Attack detection is a critical component of cybersecurity, as it can help organizations to protect their data and systems from unauthorized access, theft, or damage. Here are five tips for effective attack detection:
Tip 1: Implement a layered security approach
A layered security approach involves using multiple security controls to protect your systems and data. This can include firewalls, intrusion detection systems, antivirus software, and access control lists. By implementing a layered security approach, you can make it more difficult for attackers to compromise your systems.
Tip 2: Keep your software up to date
Software updates often include security patches that fix vulnerabilities that could be exploited by attackers. By keeping your software up to date, you can reduce the risk of successful attacks.
Tip 3: Use strong passwords
Strong passwords are essential for protecting your accounts from unauthorized access. A strong password should be at least 12 characters long and contain a mix of upper and lower case letters, numbers, and symbols. You should also avoid using common words or phrases.
Tip 4: Educate your employees about cybersecurity
Your employees are your first line of defense against cyberattacks. By educating your employees about cybersecurity, you can help them to identify and report suspicious activity.
Tip 5: Monitor your systems for suspicious activity
Regularly monitoring your systems for suspicious activity can help you to identify and respond to attacks quickly. You can use security tools, such as intrusion detection systems and security information and event management (SIEM) systems, to monitor your systems for suspicious activity.
Summary
By following these tips, you can improve your organization’s security posture and reduce the risk of successful attacks.
Conclusion
Attack detection is a critical component of cybersecurity, as it can help organizations to protect their data and systems from unauthorized access, theft, or damage. By implementing effective attack detection measures, organizations can reduce the risk of successful attacks and protect their sensitive information.
Attack detection is an ongoing process, and organizations should regularly review their security measures and update their attack detection systems to keep up with the latest threats. By staying ahead of the curve, organizations can protect their data and systems from the ever-evolving threat of cyberattacks.
Youtube Video: