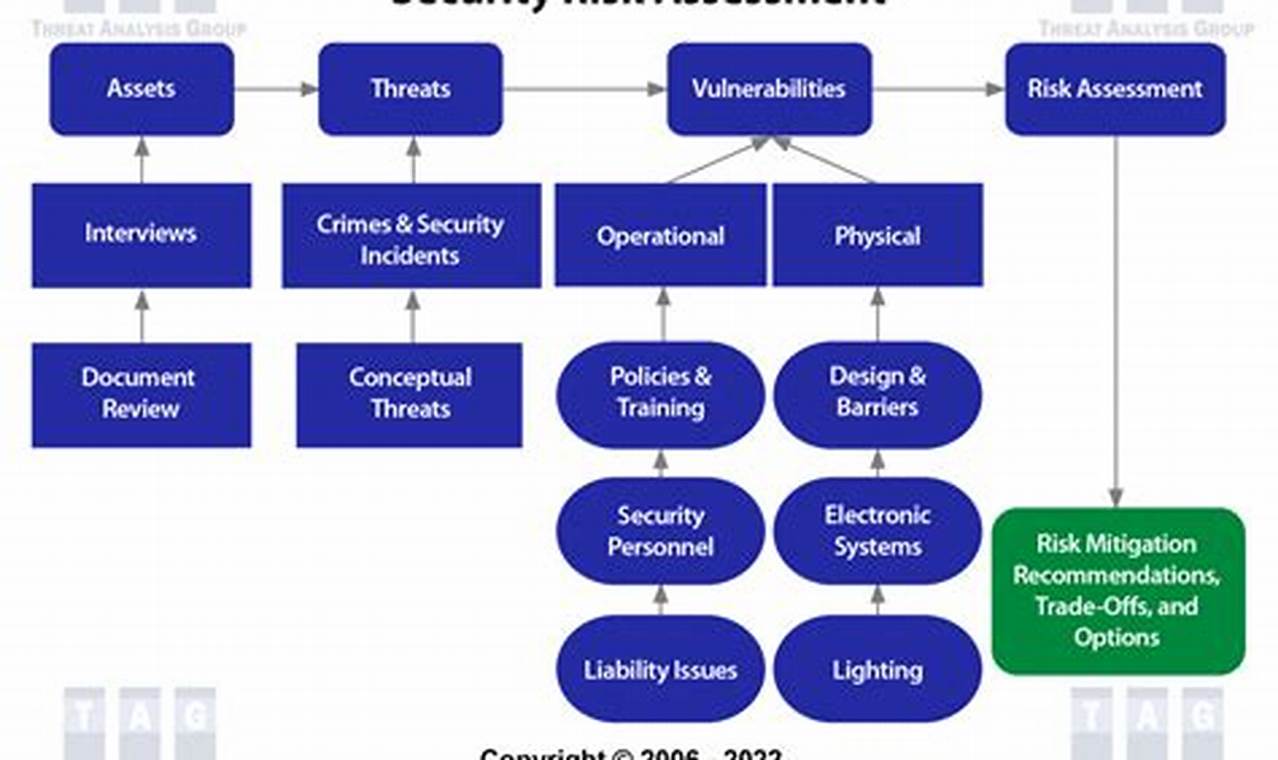
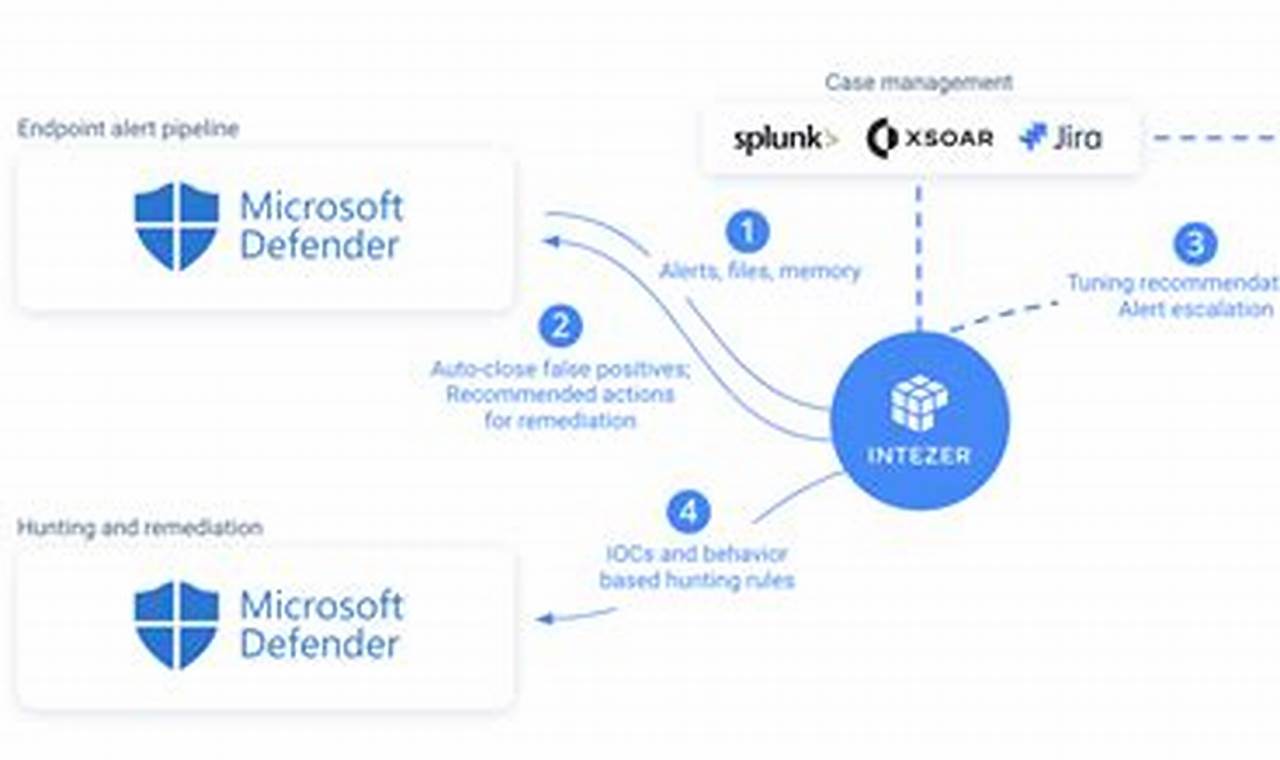
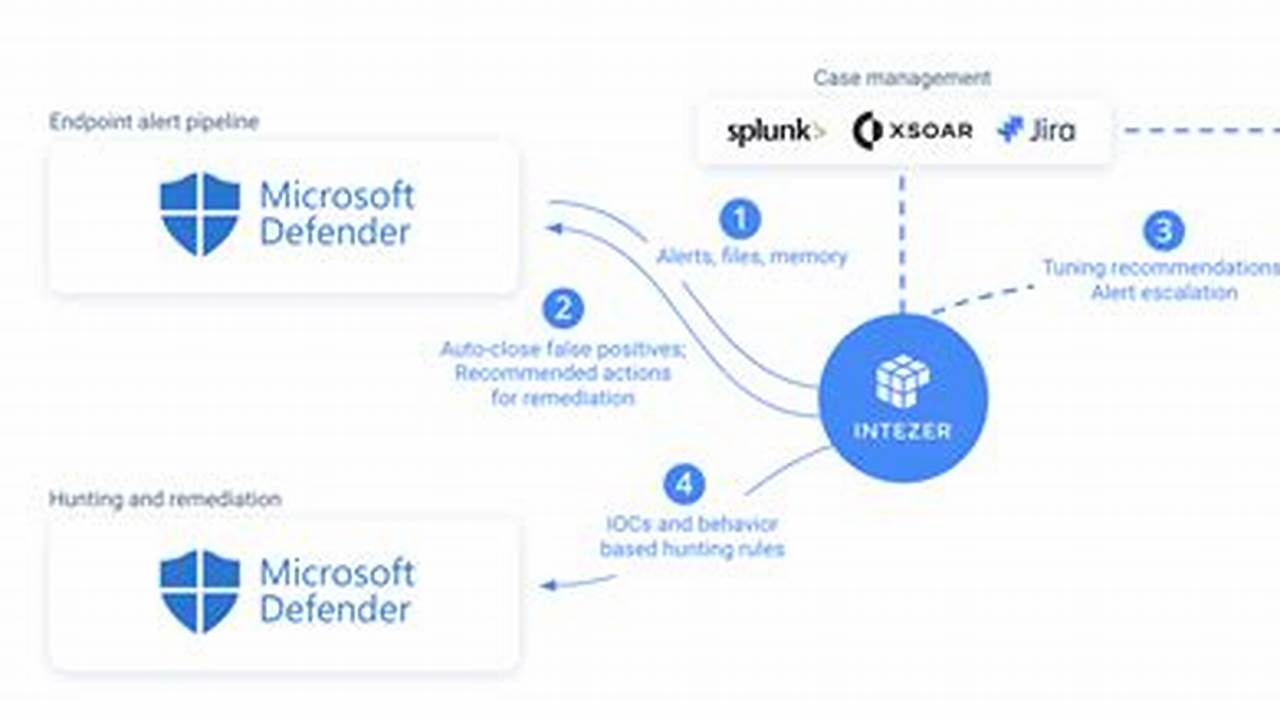
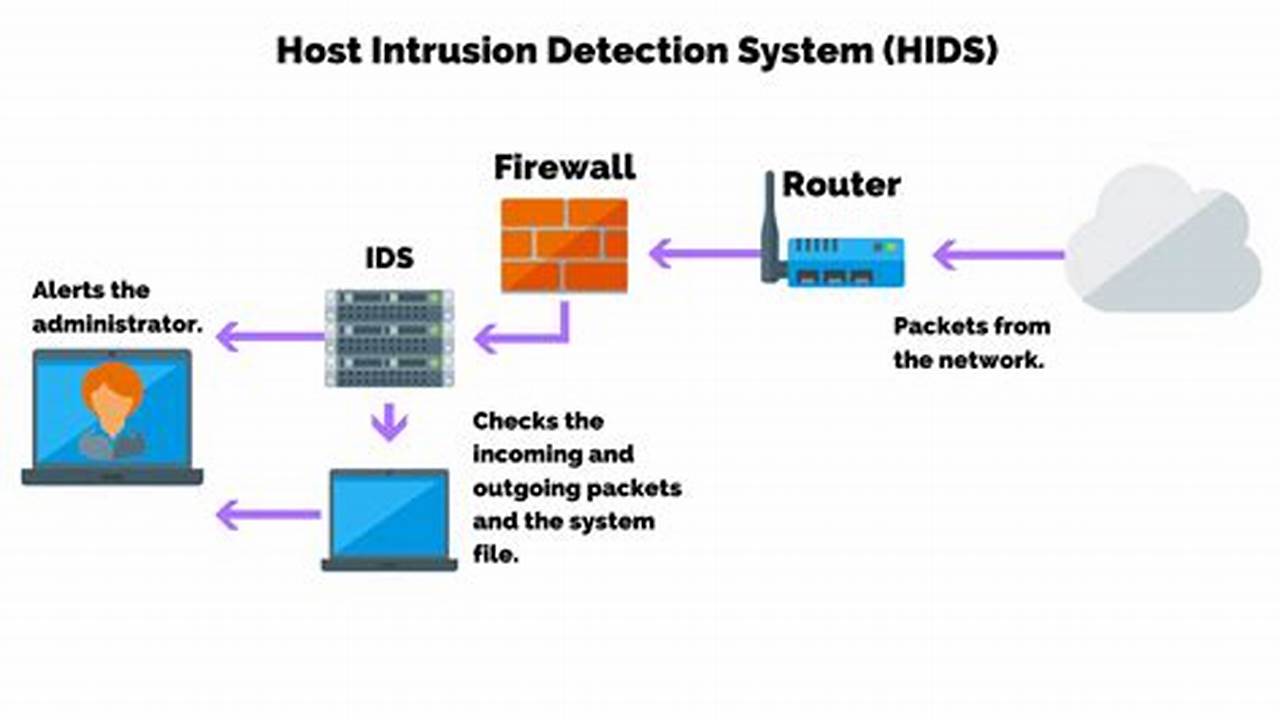
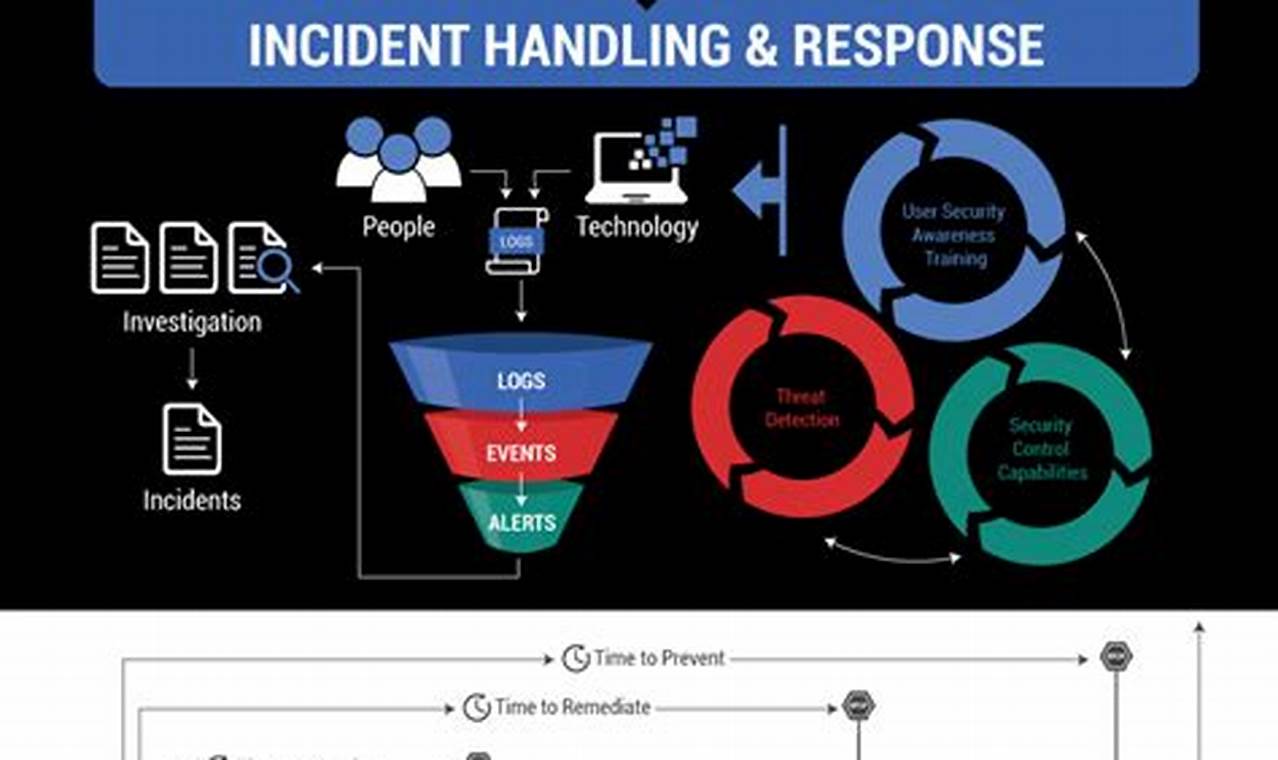
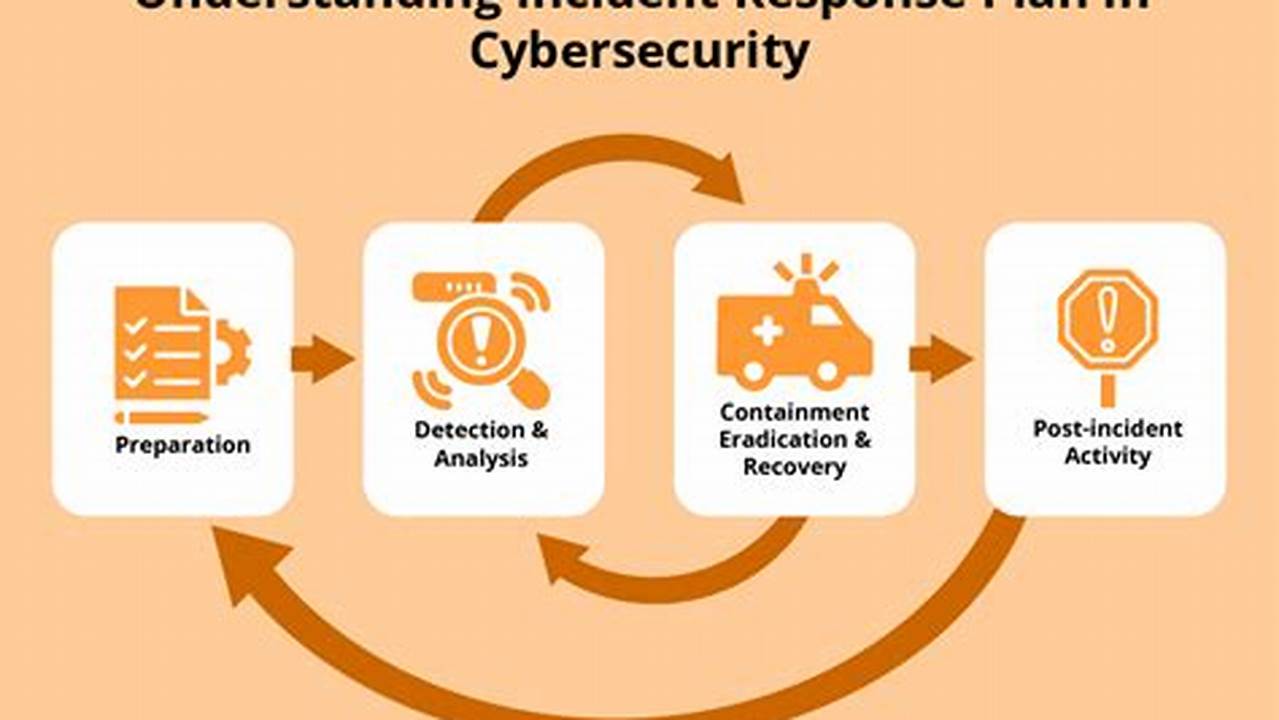
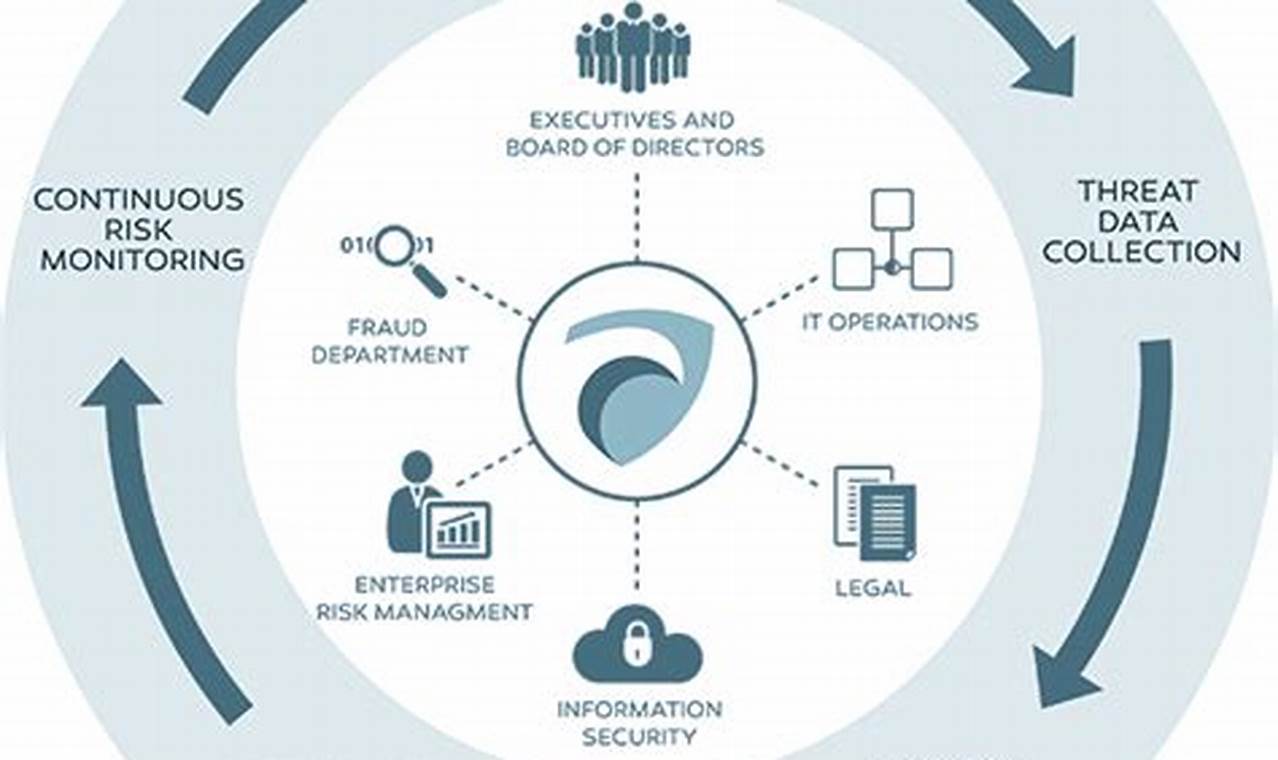
Security risk management is a crucial aspect of safeguarding sensitive information and critical assets against potential threats and vulnerabilities. It involves identifying, assessing, and mitigating risks that could compromise the integrity, confidentiality, and availability of an organization’s assets and operations.
Effective security risk management is vital as it helps organizations prioritize and address their most critical risks, ensuring business continuity, reputational protection, and compliance with regulatory requirements. It enables organizations to allocate resources efficiently, make informed decisions, and reduce the likelihood and impact of potential incidents.