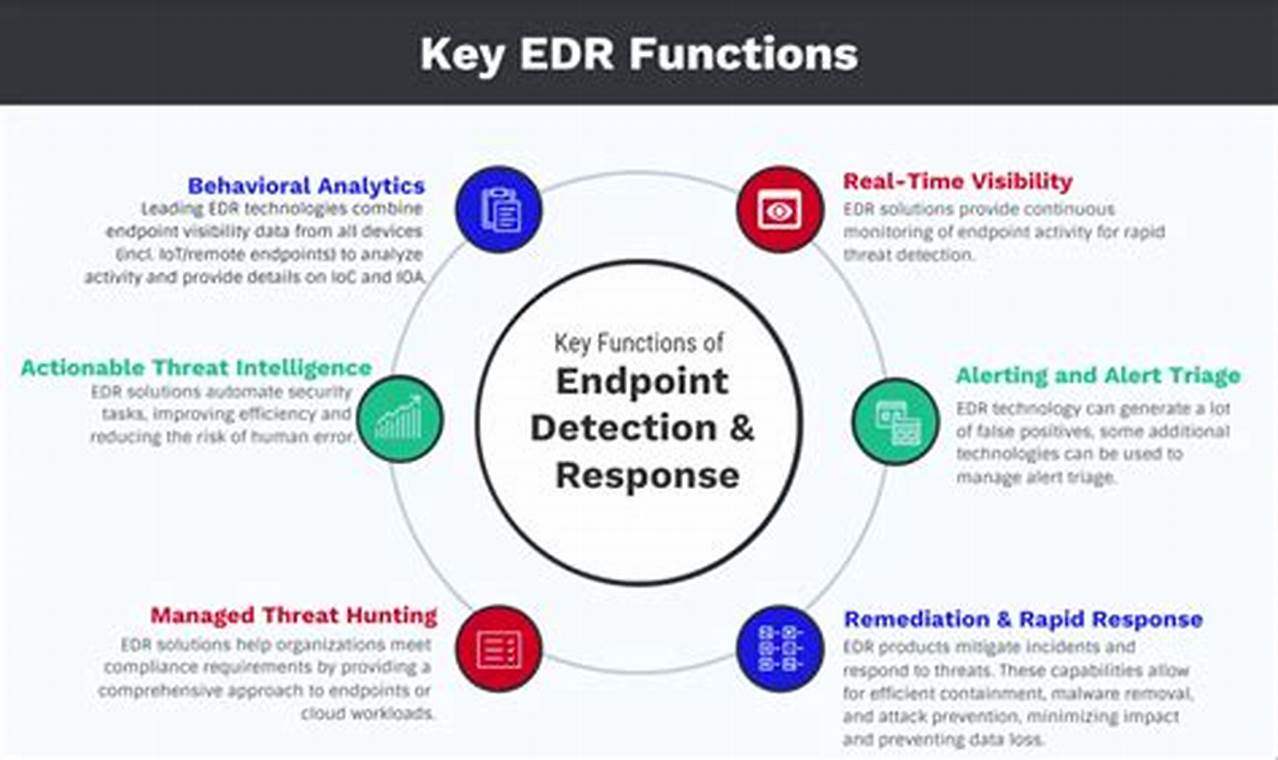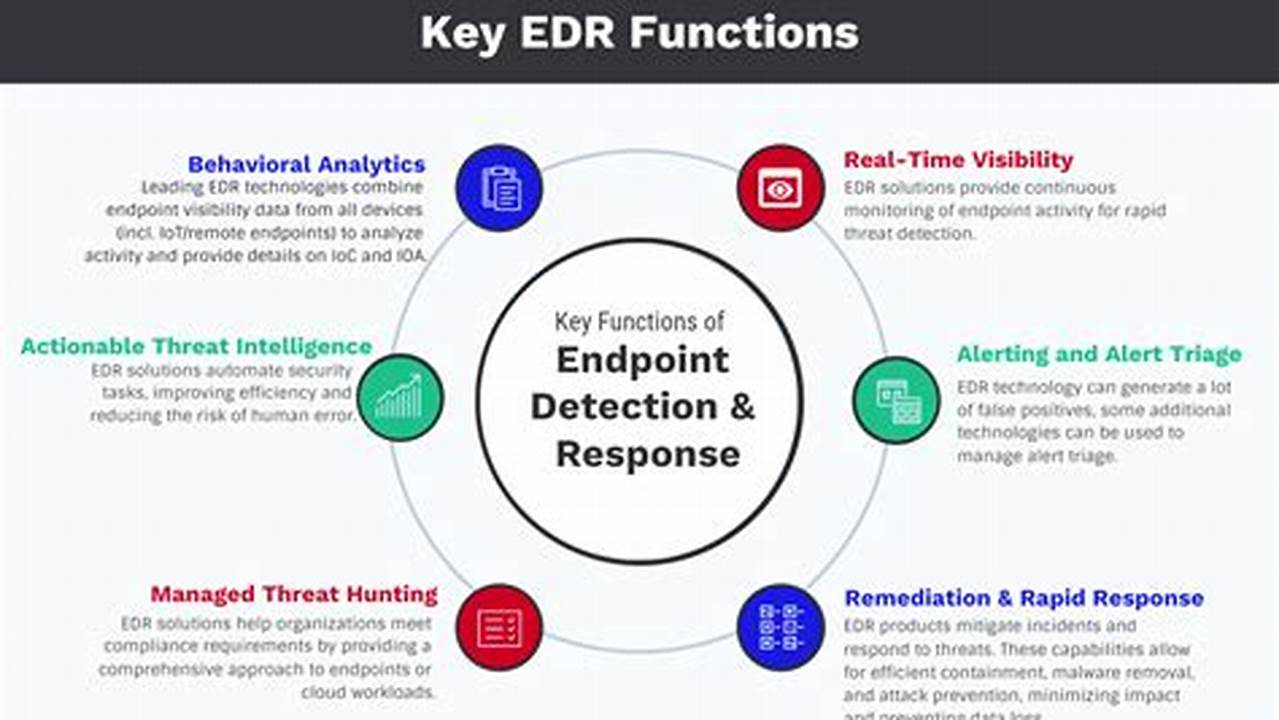
Endpoint detection technology (EDT) is a proactive cybersecurity solution that monitors endpoints, such as laptops, desktops, and mobile devices, for suspicious activities. It uses a variety of techniques, including machine learning and behavioral analysis, to detect and respond to threats in real time.
EDT is important because it can help organizations to protect themselves from a variety of threats, including malware, ransomware, and phishing attacks. It can also help to improve compliance with industry regulations and standards. EDT has become increasingly important in recent years as the number of cyberattacks has increased and the sophistication of these attacks has grown.
There are a number of different EDT solutions available on the market, and organizations should carefully evaluate their options before selecting a solution. The best EDT solution for an organization will depend on its specific needs and requirements.
Endpoint detection technology
Endpoint detection technology (EDT) is a critical component of any modern cybersecurity strategy. It provides organizations with the ability to detect and respond to threats in real time, protecting their data and systems from compromise. There are a number of key aspects to EDT that organizations should be aware of, including:
- Detection techniques: EDT uses a variety of techniques to detect threats, including signature-based detection, anomaly detection, and behavioral analysis.
- Response capabilities: EDT can be configured to automatically respond to threats, such as by blocking malicious traffic or quarantining infected files.
- Integration with other security tools: EDT can be integrated with other security tools, such as firewalls and intrusion detection systems, to provide a comprehensive defense against cyber threats.
- Cloud-based delivery: EDT can be delivered from the cloud, which makes it easy to deploy and manage.
- Scalability: EDT can be scaled to meet the needs of any organization, regardless of its size or complexity.
- Cost-effectiveness: EDT is a cost-effective way to protect an organization’s data and systems from cyber threats.
- Ease of use: EDT is easy to deploy and manage, even for organizations with limited IT resources.
- Compliance: EDT can help organizations to comply with industry regulations and standards.
These are just a few of the key aspects of EDT that organizations should be aware of. By understanding these aspects, organizations can make informed decisions about how to implement and use EDT to protect their data and systems from cyber threats.
Detection techniques
Endpoint detection technology (EDT) relies on a range of detection techniques to identify and respond to threats. These techniques include signature-based detection, anomaly detection, and behavioral analysis.
- Signature-based detection compares files and network traffic to known threat signatures. When a match is found, the EDT solution alerts the administrator and takes appropriate action, such as blocking the file or traffic.
- Anomaly detection monitors system activity for deviations from normal behavior. When an anomaly is detected, the EDT solution investigates and determines whether it is a threat.
- Behavioral analysis monitors user and system behavior for suspicious patterns. When a suspicious pattern is detected, the EDT solution investigates and determines whether it is a threat.
By using a combination of these detection techniques, EDT solutions can effectively identify and respond to a wide range of threats, including malware, ransomware, and phishing attacks.
Response capabilities
The response capabilities of endpoint detection technology (EDT) are a critical part of its effectiveness. EDT solutions can be configured to automatically respond to threats in a variety of ways, such as by blocking malicious traffic, quarantining infected files, or terminating malicious processes. This automated response can help to prevent threats from compromising an organization’s data and systems.
- Immediate response: EDT solutions can be configured to respond to threats immediately, without waiting for human intervention. This is important for preventing threats from spreading and causing damage.
- Customizable responses: EDT solutions can be customized to respond to different types of threats in different ways. For example, an EDT solution could be configured to block malicious traffic from a specific IP address, or to quarantine infected files in a specific folder.
- Integration with other security tools: EDT solutions can be integrated with other security tools, such as firewalls and intrusion detection systems, to provide a comprehensive defense against cyber threats.
The response capabilities of EDT are a powerful tool for protecting organizations from cyber threats. By automating the response to threats, EDT solutions can help to prevent threats from compromising an organization’s data and systems.
Integration with other security tools
Endpoint detection technology (EDT) is a critical component of a comprehensive cybersecurity strategy. By integrating EDT with other security tools, organizations can create a defense-in-depth strategy that can help to protect against a wide range of cyber threats.
- Improved threat detection: EDT can be integrated with firewalls to detect and block malicious traffic at the network level. This can help to prevent threats from entering the network in the first place.
- Enhanced response capabilities: EDT can be integrated with intrusion detection systems to provide automated responses to threats. This can help to prevent threats from spreading and causing damage.
- Centralized management: EDT can be integrated with a centralized management console to provide a single pane of glass for managing all of an organization’s security tools. This can help to improve efficiency and reduce the risk of security breaches.
By integrating EDT with other security tools, organizations can create a more comprehensive and effective defense against cyber threats. This can help to protect data, systems, and reputation.
Cloud-based delivery
Cloud-based delivery of endpoint detection technology (EDT) has revolutionized the way that organizations protect their endpoints from cyber threats. In the past, EDT solutions were typically deployed on-premises, which required organizations to purchase and maintain hardware and software. This could be a costly and time-consuming process.
- Reduced costs: Cloud-based EDT solutions are typically less expensive than on-premises solutions because organizations do not have to purchase and maintain hardware and software.
- Faster deployment: Cloud-based EDT solutions can be deployed quickly and easily, without the need for extensive configuration or maintenance.
- Improved scalability: Cloud-based EDT solutions can be easily scaled to meet the needs of an organization, regardless of its size or complexity.
- Access to the latest features: Cloud-based EDT solutions are always up-to-date with the latest features and functionality, without the need for manual updates.
As a result of these benefits, cloud-based EDT solutions are becoming increasingly popular with organizations of all sizes. Cloud-based EDT solutions provide organizations with a more cost-effective, efficient, and scalable way to protect their endpoints from cyber threats.
Scalability
Endpoint detection technology (EDT) is a critical component of any modern cybersecurity strategy. It provides organizations with the ability to detect and respond to threats in real time, protecting their data and systems from compromise. One of the key advantages of EDT is its scalability. EDT solutions can be scaled to meet the needs of any organization, regardless of its size or complexity.
- Number of endpoints: EDT solutions can be scaled to protect any number of endpoints, from a few dozen to thousands or even millions.
- Geographic distribution: EDT solutions can be deployed across multiple locations, regardless of their geographic distribution.
- Variety of endpoints: EDT solutions can protect a wide variety of endpoints, including laptops, desktops, servers, and mobile devices.
- Complexity of environment: EDT solutions can be deployed in complex environments, such as those with multiple operating systems and applications.
The scalability of EDT solutions is a major advantage for organizations of all sizes. It allows organizations to protect their entire IT infrastructure from cyber threats, regardless of their size or complexity. This can help organizations to improve their security posture and reduce their risk of a data breach.
Cost-effectiveness
Endpoint detection technology (EDT) is a cost-effective way to protect an organization’s data and systems from cyber threats. EDT solutions are typically less expensive than traditional security solutions, such as firewalls and intrusion detection systems. This is because EDT solutions are typically deployed on a per-endpoint basis, which means that organizations only pay for the number of endpoints that they need to protect.
- Reduced hardware costs: EDT solutions do not require organizations to purchase and maintain dedicated hardware appliances. This can save organizations a significant amount of money, especially for organizations with a large number of endpoints.
- Reduced software costs: EDT solutions typically use open source software, which is free to use and distribute. This can save organizations a significant amount of money on software licensing costs.
- Reduced maintenance costs: EDT solutions are typically easy to deploy and maintain. This can save organizations a significant amount of money on IT staff costs.
In addition to these cost savings, EDT solutions can also help organizations to improve their security posture. EDT solutions can detect and respond to threats in real time, which can help organizations to prevent data breaches and other security incidents. This can save organizations a significant amount of money in the long run.
Ease of use
Endpoint detection technology (EDT) is a powerful tool for protecting organizations from cyber threats. However, EDT solutions can be complex and difficult to deploy and manage, especially for organizations with limited IT resources. This is where ease of use becomes a critical factor.
EDT solutions that are easy to deploy and manage can be implemented quickly and efficiently, even by organizations with limited IT resources. This can help organizations to improve their security posture and reduce their risk of a data breach. In addition, easy-to-use EDT solutions can help organizations to save money on IT staff costs.
There are a number of factors that contribute to the ease of use of an EDT solution. These factors include:
- Simple deployment: EDT solutions that are easy to deploy can be installed and configured quickly and easily, without requiring extensive technical expertise.
- Intuitive interface: EDT solutions that have an intuitive interface are easy to use and navigate, even for users with limited IT experience.
- Automated updates: EDT solutions that automatically update their signatures and definitions are easy to maintain, and they help to ensure that organizations are protected from the latest threats.
Organizations that are looking for an EDT solution should consider ease of use as a key factor in their decision-making process. EDT solutions that are easy to deploy and manage can help organizations to improve their security posture, reduce their risk of a data breach, and save money on IT staff costs.
Compliance
Endpoint detection technology (EDT) plays a crucial role in helping organizations comply with industry regulations and standards. By providing real-time monitoring and detection of threats, EDT solutions can help organizations to protect their data and systems from unauthorized access, data breaches, and other security incidents. This can help organizations to avoid costly fines and penalties, as well as reputational damage.
- PCI DSS: The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards that organizations must comply with in order to process, store, and transmit credit card data. EDT solutions can help organizations to comply with PCI DSS by detecting and preventing unauthorized access to credit card data, as well as by monitoring for suspicious activity that could indicate a data breach.
- HIPAA: The Health Insurance Portability and Accountability Act (HIPAA) is a set of federal regulations that protect the privacy and security of health information. EDT solutions can help organizations to comply with HIPAA by detecting and preventing unauthorized access to health information, as well as by monitoring for suspicious activity that could indicate a data breach.
- GDPR: The General Data Protection Regulation (GDPR) is a European Union regulation that protects the privacy and security of personal data. EDT solutions can help organizations to comply with GDPR by detecting and preventing unauthorized access to personal data, as well as by monitoring for suspicious activity that could indicate a data breach.
- ISO 27001: ISO 27001 is an international standard that specifies the requirements for an information security management system (ISMS). EDT solutions can help organizations to comply with ISO 27001 by providing real-time monitoring and detection of threats, as well as by providing evidence of compliance to auditors.
These are just a few of the many industry regulations and standards that EDT solutions can help organizations to comply with. By implementing an EDT solution, organizations can improve their security posture, reduce their risk of a data breach, and avoid costly fines and penalties.
Endpoint Detection Technology FAQs
This section addresses frequently asked questions and misconceptions about endpoint detection technology (EDT).
Question 1: What is endpoint detection technology (EDT)?
Answer: Endpoint detection technology (EDT) is a cybersecurity solution that monitors endpoints, such as laptops, desktops, and mobile devices, for suspicious activities. It uses a variety of techniques, including machine learning and behavioral analysis, to detect and respond to threats in real time.
Question 2: Why is EDT important?
Answer: EDT is important because it can help organizations to protect themselves from a variety of threats, including malware, ransomware, and phishing attacks. It can also help to improve compliance with industry regulations and standards.
Question 3: How does EDT work?
Answer: EDT works by monitoring endpoints for suspicious activities. When suspicious activity is detected, EDT can take a variety of actions, such as blocking the malicious activity, quarantining the infected file, or alerting the administrator.
Question 4: What are the benefits of using EDT?
Answer: There are many benefits to using EDT, including improved security, reduced risk of data breaches, and improved compliance with industry regulations and standards.
Question 5: What are the challenges of using EDT?
Answer: There are some challenges to using EDT, such as the cost of implementation and the need for skilled personnel to manage the solution.
Question 6: What are the future trends in EDT?
Answer: The future of EDT is bright. As the number of cyber threats continues to grow, so too will the demand for EDT solutions. We can expect to see continued innovation in EDT, with new features and capabilities being added all the time.
Summary: Endpoint detection technology (EDT) is a critical component of any modern cybersecurity strategy. It can help organizations to protect themselves from a variety of threats, improve compliance with industry regulations and standards, and reduce the risk of data breaches.
Transition to the next article section: For more information on endpoint detection technology, please refer to the following resources:
Endpoint Detection Technology Tips
Endpoint detection technology (EDT) is a critical component of any modern cybersecurity strategy. It can help organizations to protect themselves from a variety of threats, improve compliance with industry regulations and standards, and reduce the risk of data breaches.
Here are five tips for using EDT effectively:
Tip 1: Choose the right EDT solution for your organization. There are a variety of EDT solutions available on the market, so it is important to choose one that is right for your organization’s needs. Consider factors such as the number of endpoints you need to protect, your budget, and your IT expertise.
Tip 2: Implement EDT correctly. Once you have chosen an EDT solution, it is important to implement it correctly. This includes installing the software on all of your endpoints, configuring the software correctly, and training your staff on how to use the software.
Tip 3: Monitor EDT alerts regularly. EDT solutions will generate alerts when they detect suspicious activity. It is important to monitor these alerts regularly and investigate any potential threats.
Tip 4: Keep EDT software up to date. EDT software is constantly being updated to detect new threats. It is important to keep your EDT software up to date to ensure that you are protected from the latest threats.
Tip 5: Use EDT in conjunction with other security measures. EDT is an important part of a comprehensive cybersecurity strategy, but it is not the only measure that you should take. Use EDT in conjunction with other security measures, such as firewalls, intrusion detection systems, and anti-malware software.
By following these tips, you can use EDT effectively to protect your organization from cyber threats.
Summary: Endpoint detection technology (EDT) is a powerful tool for protecting organizations from cyber threats. By following these tips, you can use EDT effectively to improve your security posture and reduce your risk of a data breach.
Transition to the article’s conclusion: For more information on endpoint detection technology, please refer to the following resources:
Endpoint Detection Technology
Endpoint detection technology (EDT) is a critical component of any modern cybersecurity strategy. It provides organizations with the ability to detect and respond to threats in real time, protecting their data and systems from compromise. EDT solutions are cost-effective, easy to deploy and manage, and can help organizations to comply with industry regulations and standards.
As the number of cyber threats continues to grow, so too will the importance of EDT. Organizations that are not using EDT are putting themselves at risk of a data breach or other security incident. By implementing an EDT solution, organizations can improve their security posture, reduce their risk of a data breach, and protect their reputation.
Youtube Video: