Host-based security refers to a comprehensive approach to protecting individual computer systems from unauthorized access, use, disclosure, disruption, modification, or destruction. Unlike network-based security, which focuses on securing the network infrastructure, host-based security measures are implemented directly on each host or endpoint device within a network.
Host-based security is vital because it safeguards individual devices from various threats and vulnerabilities. It can prevent malware infections, unauthorized access to sensitive data, and system disruptions. Implementing host-based security measures like antivirus software, firewalls, intrusion detection systems, and access controls enhances the overall security posture of an organization by securing each device within the network.
In essence, host-based security serves as a cornerstone of a robust cybersecurity strategy, complementing network-based security measures to provide a holistic approach to protecting an organization’s IT infrastructure. By securing individual devices, organizations can effectively mitigate risks, maintain data integrity, and ensure the smooth operation of their systems.
Host-based security
Host-based security is a critical aspect of cybersecurity, safeguarding individual computer systems from various threats and vulnerabilities. Here are six key aspects that underscore its importance:
- Malware Protection: Prevents malware infections and their potential damage.
- Unauthorized Access Control: Restricts unauthorized access to sensitive data and system resources.
- Vulnerability Management: Identifies and patches vulnerabilities to mitigate security risks.
- Intrusion Detection: Monitors system activity for suspicious patterns and alerts of potential threats.
- Log Monitoring: Records and analyzes system events to detect anomalies and potential security breaches.
- Patch Management: Ensures timely installation of security updates to address vulnerabilities.
These key aspects work together to provide comprehensive protection for individual devices within a network. By implementing strong host-based security measures, organizations can significantly enhance their overall security posture, reduce the risk of data breaches and system disruptions, and maintain the integrity and availability of their IT infrastructure.
Malware Protection
Malware protection is a crucial aspect of host-based security, safeguarding individual computer systems from malicious software infections and their potential consequences. Malware, short for malicious software, encompasses a wide range of threats, including viruses, worms, Trojans, ransomware, and spyware, each designed to exploit vulnerabilities and cause varying degrees of damage.
- Infection Prevention: Malware protection tools, such as antivirus and anti-malware software, act as a first line of defense against malware infections. They scan files, emails, and network traffic for malicious code and prevent their execution or installation.
- Real-time Monitoring: Advanced malware protection solutions employ real-time monitoring capabilities to detect and block malware even before they can infect a system. They use behavioral analysis and machine learning algorithms to identify suspicious activities and take appropriate action.
- Quarantine and Removal: When malware is detected, malware protection tools quarantine or remove it from the system, preventing it from causing further damage. They also provide options for restoring infected files and systems to a clean state.
- Automatic Updates: Malware protection software regularly releases updates to its virus definitions and threat intelligence to stay abreast of the latest malware threats. Automatic updates ensure that systems are protected against emerging malware variants.
Effective malware protection is essential for host-based security as it safeguards individual devices from the damaging effects of malware infections. By preventing malware from executing, stealing sensitive data, or disrupting system operations, malware protection contributes to the overall security and stability of an organization’s IT infrastructure.
Unauthorized Access Control
Unauthorized access control is a fundamental aspect of host-based security, safeguarding individual computer systems from unauthorized access to sensitive data and system resources. It involves implementing measures to prevent malicious actors or unauthorized users from gaining access to critical information or resources within a network.
- Authentication and Authorization: Authentication mechanisms verify the identity of users attempting to access a system or resource, while authorization mechanisms determine the level of access granted based on predefined rules and permissions.
- Access Control Lists (ACLs): ACLs are security features that specify which users or groups have permission to access specific files, directories, or system resources.
- Role-Based Access Control (RBAC): RBAC is a security model that assigns permissions and access rights based on the roles of users within an organization, ensuring that users only have access to the resources necessary for their job functions.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide multiple forms of identification when logging in to a system or accessing sensitive data.
Unauthorized access control plays a vital role in host-based security by preventing unauthorized individuals from accessing sensitive data or disrupting system operations. By implementing robust access control measures, organizations can protect their confidential information, maintain the integrity of their systems, and comply with industry regulations and standards.
Vulnerability Management
In the context of host-based security, vulnerability management plays a critical role in mitigating security risks by proactively identifying and patching vulnerabilities in individual computer systems. Vulnerabilities are weaknesses or flaws in software, hardware, or configurations that can be exploited by attackers to gain unauthorized access, compromise data, or disrupt system operations.
- Regular Vulnerability Scanning: Vulnerability management involves regular scanning of systems to identify potential vulnerabilities, including missing security patches, outdated software, or misconfigured settings.
- Prioritization and Remediation: Once vulnerabilities are identified, they are prioritized based on their severity and potential impact. Critical vulnerabilities are addressed immediately through patching or mitigation strategies.
- Software Updates and Patch Management: Vulnerability management includes the timely installation of security patches and updates from software vendors to address known vulnerabilities and prevent their exploitation.
- Configuration Hardening: It also involves hardening system configurations to reduce the attack surface and mitigate the impact of vulnerabilities that cannot be immediately patched.
Effective vulnerability management is crucial for host-based security as it enables organizations to proactively identify and address vulnerabilities before they can be exploited by attackers. By implementing a comprehensive vulnerability management program, organizations can significantly reduce their exposure to security risks, protect sensitive data, and maintain the integrity and availability of their IT infrastructure.
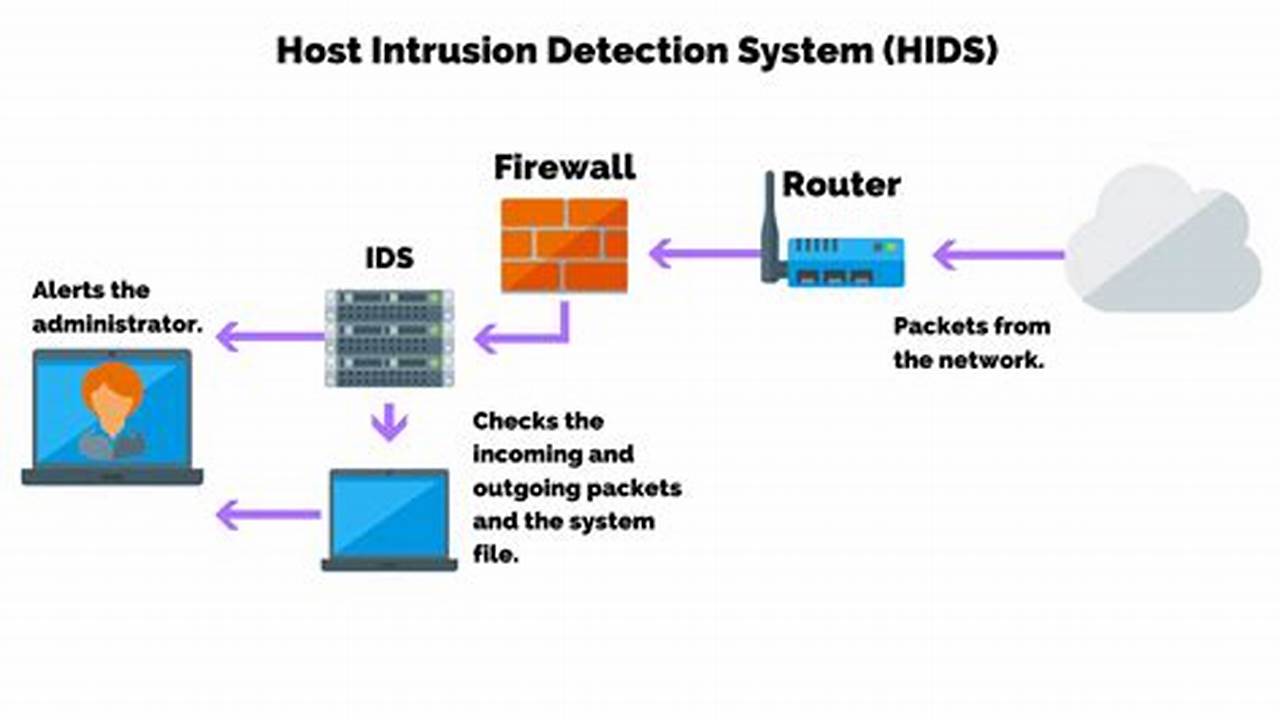
Intrusion Detection
Intrusion detection is a critical component of host-based security, providing real-time monitoring of system activity to detect and alert on potential threats. By analyzing system logs, network traffic, and other system events, intrusion detection systems (IDS) can identify suspicious patterns and behaviors that may indicate an attack or security breach.
- Signature-Based Detection: IDS can use signature-based detection to identify known attack patterns and malicious activities by matching system activity against a database of known threats.
- Anomaly-Based Detection: IDS can also use anomaly-based detection to identify deviations from normal system behavior. By establishing a baseline of expected activity, IDS can detect unusual patterns or events that may indicate an attack.
- Host-Based IDS (HIDS): HIDS are installed directly on individual host systems and monitor system activity at the operating system level, providing visibility into system events, file changes, and other critical system information.
- Network-Based IDS (NIDS): NIDS are deployed on the network and monitor network traffic for suspicious patterns and malicious activities, providing a broader view of potential threats across the network.
Intrusion detection plays a vital role in host-based security by providing early warning of potential threats. By detecting suspicious activities and alerting security teams, intrusion detection systems enable organizations to respond quickly and effectively to security incidents, minimizing the impact of attacks and protecting sensitive data and systems.
Log Monitoring
Log monitoring is a crucial aspect of host-based security, providing organizations with valuable insights into system activity and security events. By collecting and analyzing system logs, organizations can detect anomalies and potential security breaches in a timely manner, enabling them to respond quickly and effectively.
- Audit Trail and Compliance: Log monitoring provides a comprehensive audit trail of system events, assisting organizations in meeting regulatory compliance requirements and demonstrating due diligence in security practices.
- Threat Detection and Analysis: Logs contain valuable information about security events, such as failed login attempts, suspicious file modifications, and unauthorized access. By analyzing these logs, organizations can identify potential threats and investigate security incidents.
- Forensic Analysis: In the event of a security breach, log monitoring provides essential data for forensic analysis. Logs can help determine the root cause of the breach, identify the compromised systems, and guide remediation efforts.
- System Optimization and Troubleshooting: Log monitoring also supports system optimization and troubleshooting. By analyzing logs, organizations can identify performance issues, configuration errors, and other system anomalies, enabling them to proactively address these issues and maintain system stability.
Log monitoring is a critical component of host-based security, providing organizations with the visibility and insights they need to detect and respond to security threats effectively. By implementing robust log monitoring practices, organizations can strengthen their security posture, protect sensitive data, and ensure the integrity and availability of their IT infrastructure.
Patch Management
Patch management is an essential component of host-based security, playing a critical role in safeguarding individual computer systems from vulnerabilities and potential threats. Vulnerabilities are weaknesses or flaws in software, hardware, or configurations that can be exploited by attackers to gain unauthorized access, compromise data, or disrupt system operations.
Timely installation of security updates and patches is crucial for mitigating these vulnerabilities and preventing attackers from exploiting them. Patch management involves regularly scanning systems for missing security updates, prioritizing and testing patches, and deploying them across the network in a timely and efficient manner.
For instance, in 2017, the WannaCry ransomware attack exploited a vulnerability in Microsoft’s operating systems. Organizations that had not applied the available security patch were heavily impacted, resulting in widespread data loss and disruption of critical services. This highlights the importance of effective patch management in preventing successful cyberattacks.
Effective patch management practices are essential for maintaining a strong security posture. By promptly addressing vulnerabilities, organizations can significantly reduce their exposure to security risks, protect sensitive data, and ensure the integrity and availability of their IT infrastructure.
Frequently Asked Questions about Host-based Security
This section addresses common questions and misconceptions surrounding host-based security to provide a comprehensive understanding of its importance and implementation.
Question 1: What is the primary objective of host-based security?
Host-based security aims to protect individual computer systems from unauthorized access, malicious software, and other threats by implementing security measures directly on each host or endpoint device within a network.
Question 2: How does host-based security differ from network-based security?
While network-based security focuses on securing the network infrastructure, host-based security specifically targets the protection of individual devices within the network. It involves implementing security measures on each host system to safeguard against vulnerabilities and threats.
Question 3: What are the key benefits of implementing host-based security?
Host-based security offers numerous advantages, including enhanced protection against malware infections, unauthorized access control, vulnerability management, intrusion detection, log monitoring, and patch management. These measures work together to safeguard individual devices and contribute to the overall security posture of an organization.
Question 4: Is host-based security sufficient to ensure complete protection against cyber threats?
While host-based security is a critical component of cybersecurity, it alone cannot guarantee complete protection. A comprehensive security strategy should combine host-based security measures with network-based security measures, regular security audits, and employee training to provide a multi-layered defense against cyber threats.
Question 5: What are some best practices for effective host-based security implementation?
Best practices include using reputable antivirus and anti-malware software, implementing strong access controls, regularly patching software and systems, monitoring system logs for suspicious activity, and educating users about cybersecurity best practices.
Question 6: How can organizations ensure the effectiveness of their host-based security measures?
Organizations should conduct regular security assessments to evaluate the effectiveness of their host-based security measures. This involves testing security controls, monitoring security logs, and reviewing security configurations. Continuous monitoring and improvement are essential for maintaining a strong security posture.
Understanding these key questions and answers provides a solid foundation for implementing and maintaining effective host-based security measures to protect individual computer systems and the overall IT infrastructure of an organization.
[Transition to the next article section]
Host-Based Security Best Practices
Implementing robust host-based security measures is crucial for protecting individual computer systems and maintaining a strong security posture. Here are several essential tips to enhance the effectiveness of host-based security:
Tip 1: Implement Multi-Layered Protection: Utilize a combination of security tools and techniques, including antivirus and anti-malware software, firewalls, intrusion detection systems, and access control mechanisms, to create a comprehensive defense system.
Tip 2: Enforce Strong Password Policies: Implement strict password requirements, such as minimum length, complexity, and regular expiration, to prevent unauthorized access to systems.
Tip 3: Keep Software Up-to-Date: Regularly install security updates and patches for operating systems, applications, and firmware to address vulnerabilities and protect against known threats.
Tip 4: Monitor System Logs and Alerts: Configure systems to generate and monitor security logs, and establish mechanisms for timely detection and response to suspicious activities.
Tip 5: Restrict Administrative Privileges: Limit the number of users with administrative privileges to minimize the risk of unauthorized changes or malicious actions.
Tip 6: Implement Access Controls: Enforce access controls to restrict unauthorized access to sensitive data, systems, and resources, both locally and remotely.
Tip 7: Educate Users: Conduct regular security awareness training for users to educate them on cybersecurity best practices, including recognizing and reporting suspicious emails or activities.
Tip 8: Conduct Regular Security Audits: Periodically assess the effectiveness of host-based security measures, identify areas for improvement, and make necessary adjustments to maintain a strong security posture.
These tips, when implemented effectively, contribute to a robust host-based security framework, safeguarding individual devices and the overall IT infrastructure from potential threats and vulnerabilities.
[Transition to the article’s conclusion]
Host-based Security
Host-based security plays a vital role in protecting individual computer systems from a wide range of threats and vulnerabilities, safeguarding sensitive data and ensuring the integrity of IT infrastructure. By implementing measures such as malware protection, access controls, vulnerability management, intrusion detection, log monitoring, and patch management, organizations can significantly enhance their overall security posture.
The importance of host-based security cannot be overstated in today’s increasingly interconnected and threat-laden digital landscape. By securing individual devices and endpoints, organizations create a strong foundation for a robust cybersecurity defense system. It is essential for organizations to prioritize the implementation and maintenance of effective host-based security measures to protect their critical assets, maintain business continuity, and uphold their reputation in the face of evolving cyber threats.
Youtube Video:


