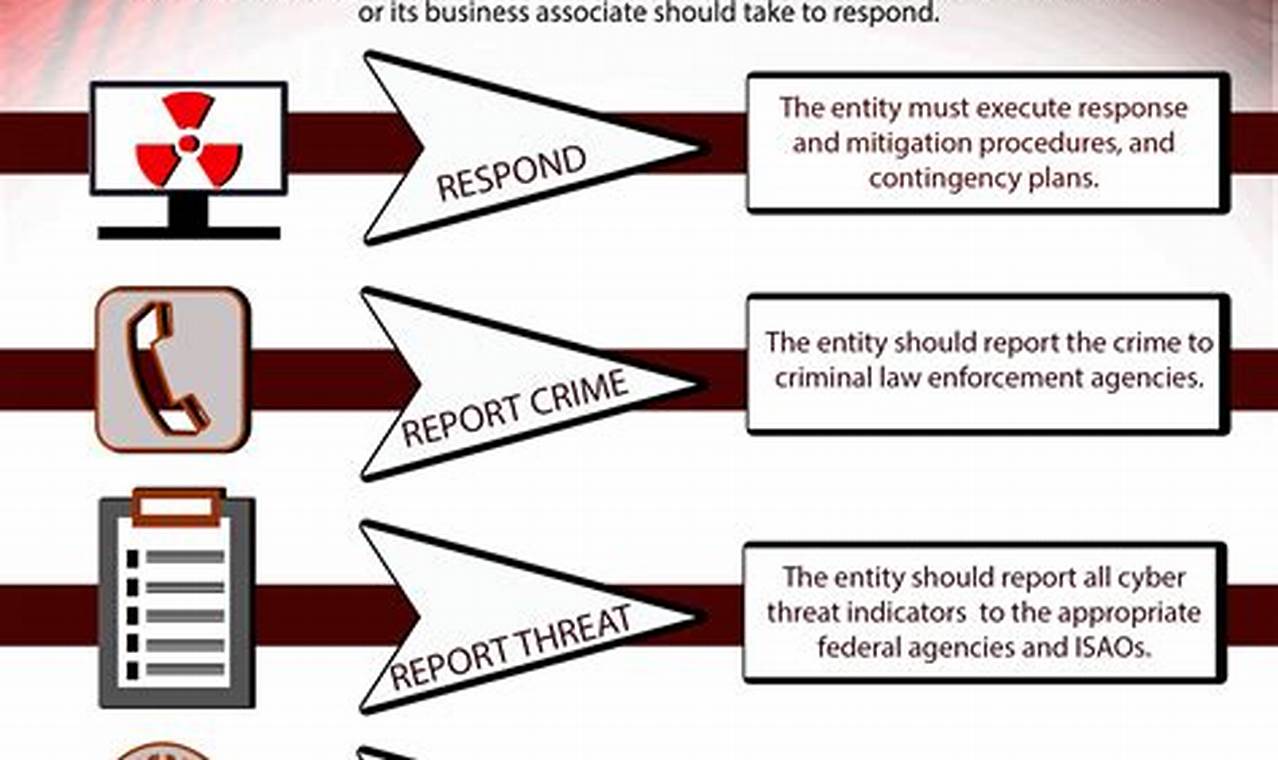
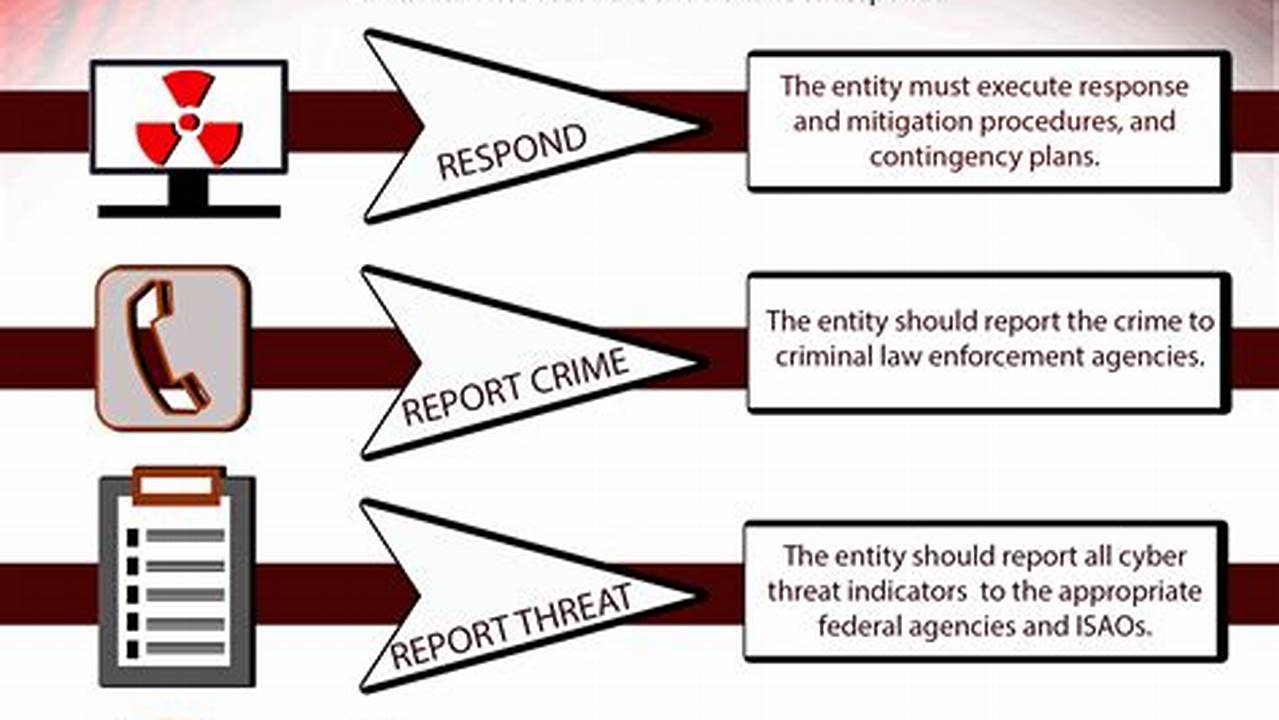
Cyber threat monitoring is the practice of continuously monitoring and analyzing networks, systems, and data for suspicious activity that could indicate a cyber attack. It involves the use of various tools and techniques to detect and respond to potential threats in real-time, enabling organizations to protect their critical assets and information.
Cyber threat monitoring plays a crucial role in preventing and mitigating cyber attacks by providing early warning and allowing organizations to take prompt action. It helps identify unauthorized access, malicious software, data breaches, and other suspicious activities, enabling security teams to investigate and respond appropriately. By continuously monitoring their systems, organizations can gain valuable insights into potential threats, emerging attack patterns, and the overall security posture of their networks.