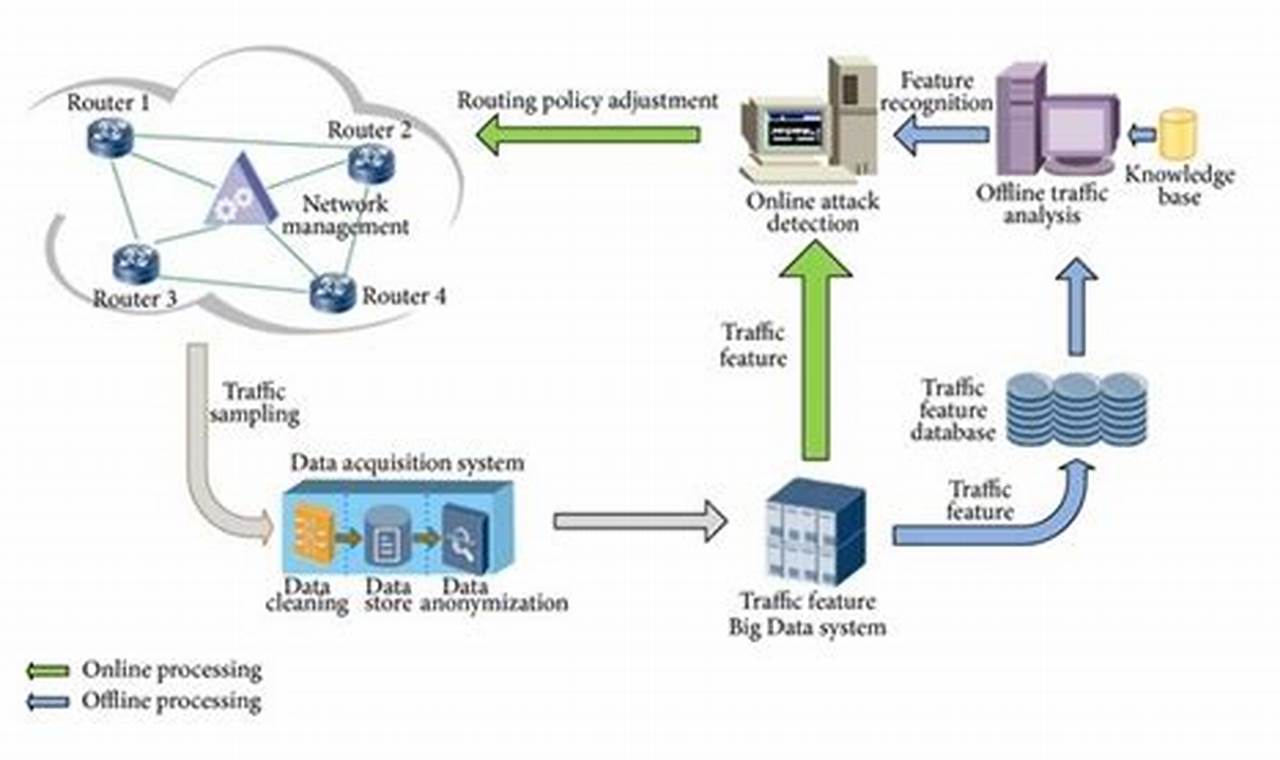
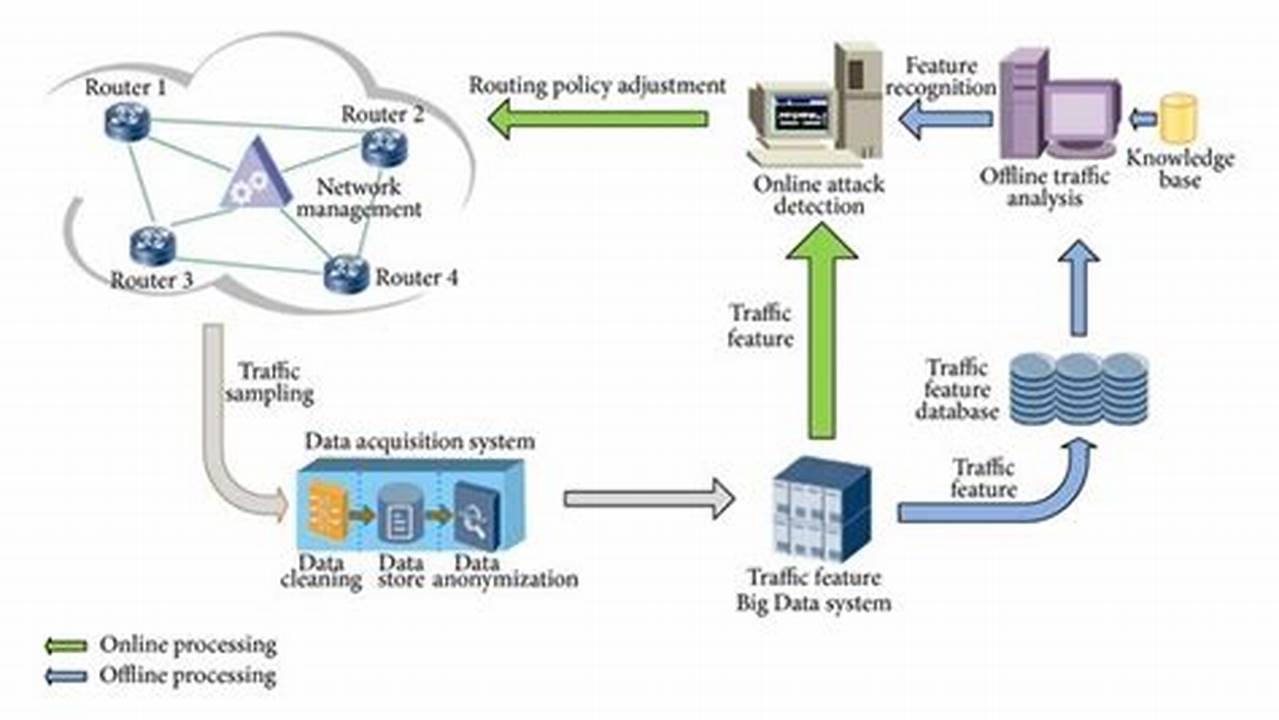
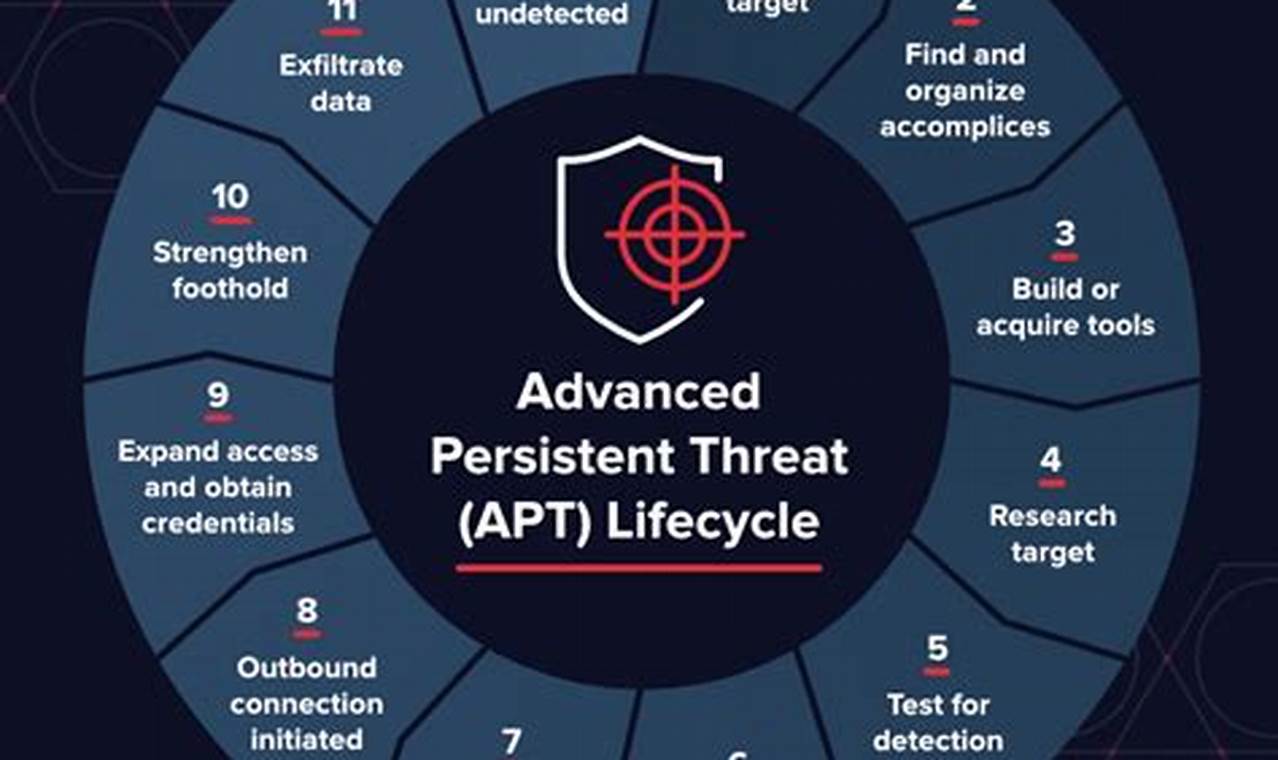
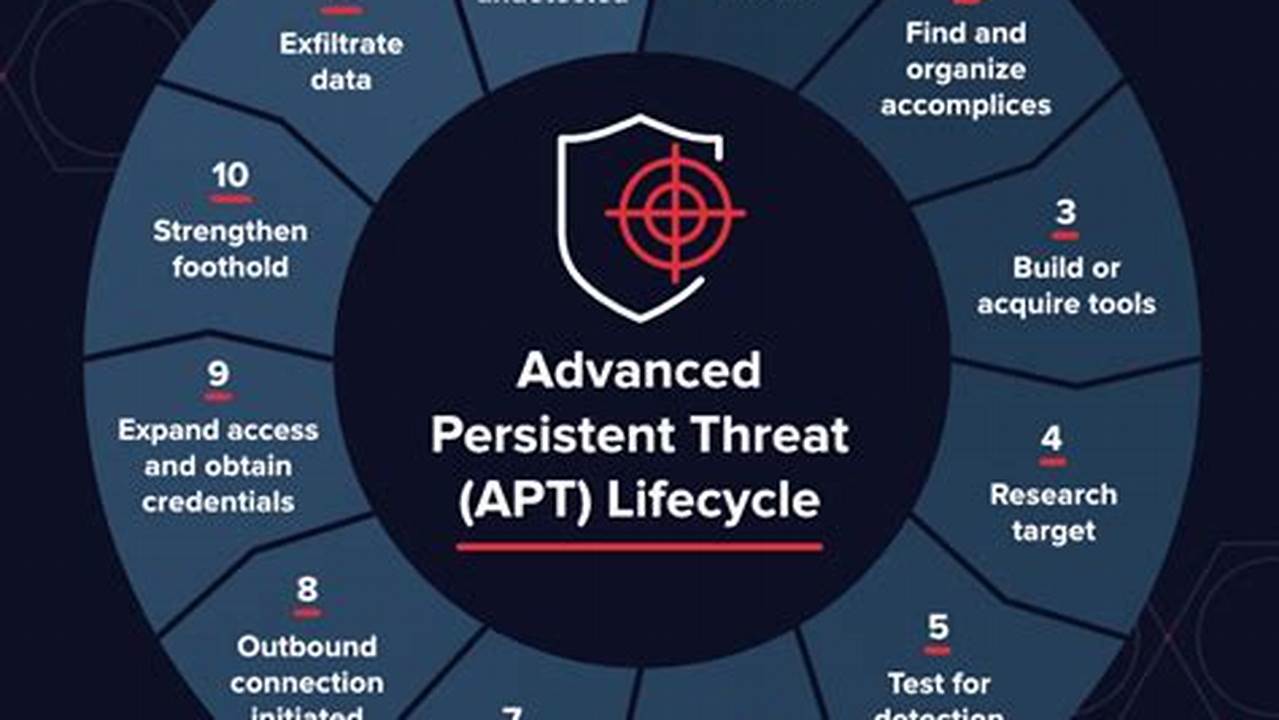
Threat detection solutions refer to technologies and services designed to identify, analyze, and respond to potential threats or vulnerabilities within a computer system or network. These solutions typically involve the use of advanced algorithms, machine learning, and continuous monitoring to detect and mitigate threats in real-time, such as malware, phishing attempts, unauthorized access, and data breaches.
Threat detection solutions play a critical role in protecting organizations and individuals from cyber threats, which have become increasingly sophisticated and targeted. By providing early detection and response capabilities, these solutions can help minimize the impact of cyberattacks, safeguard sensitive data, and ensure the continuity of operations. Threat detection solutions are also essential for meeting regulatory compliance requirements and maintaining a strong security posture.