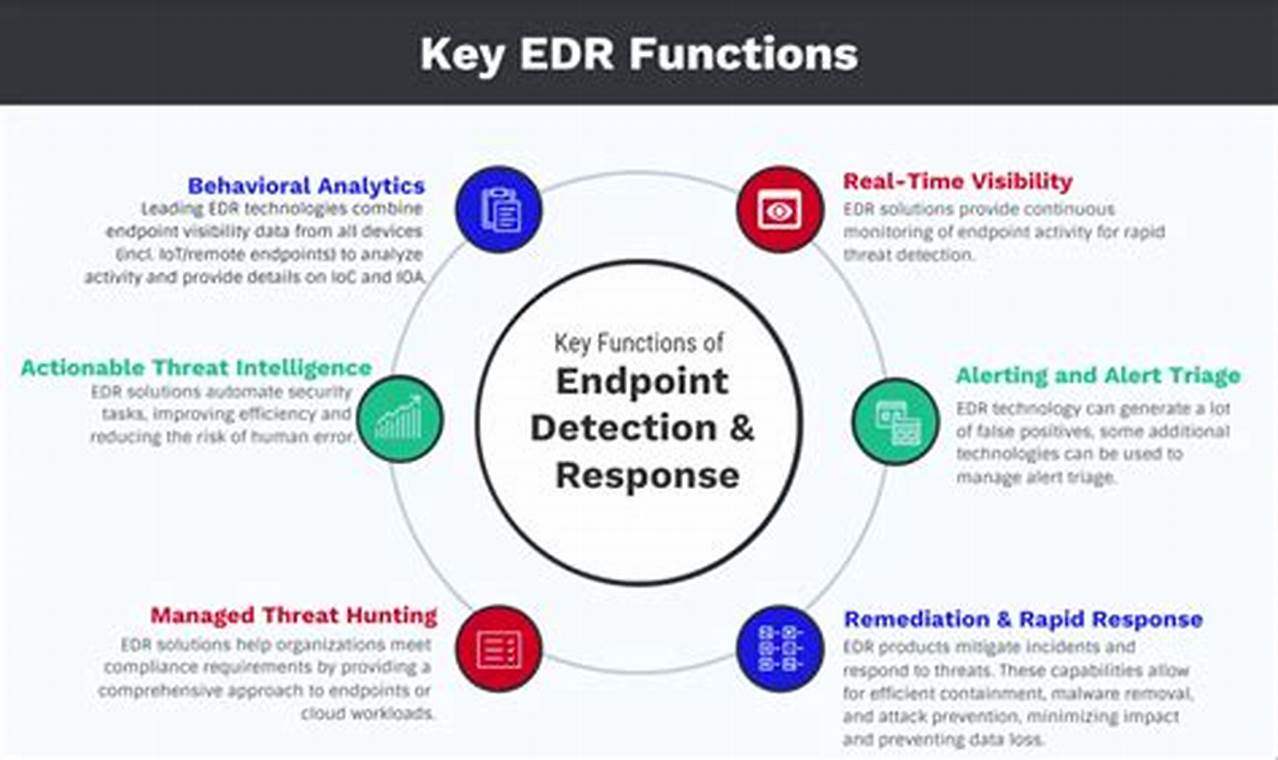
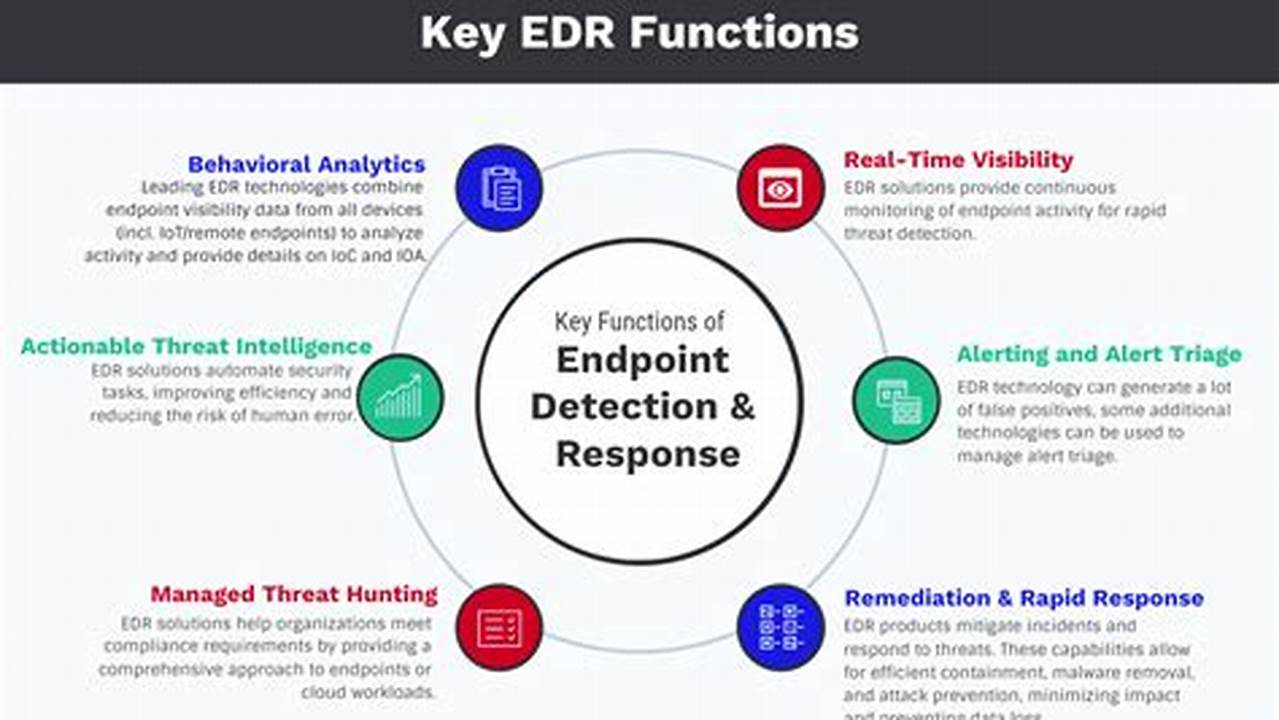
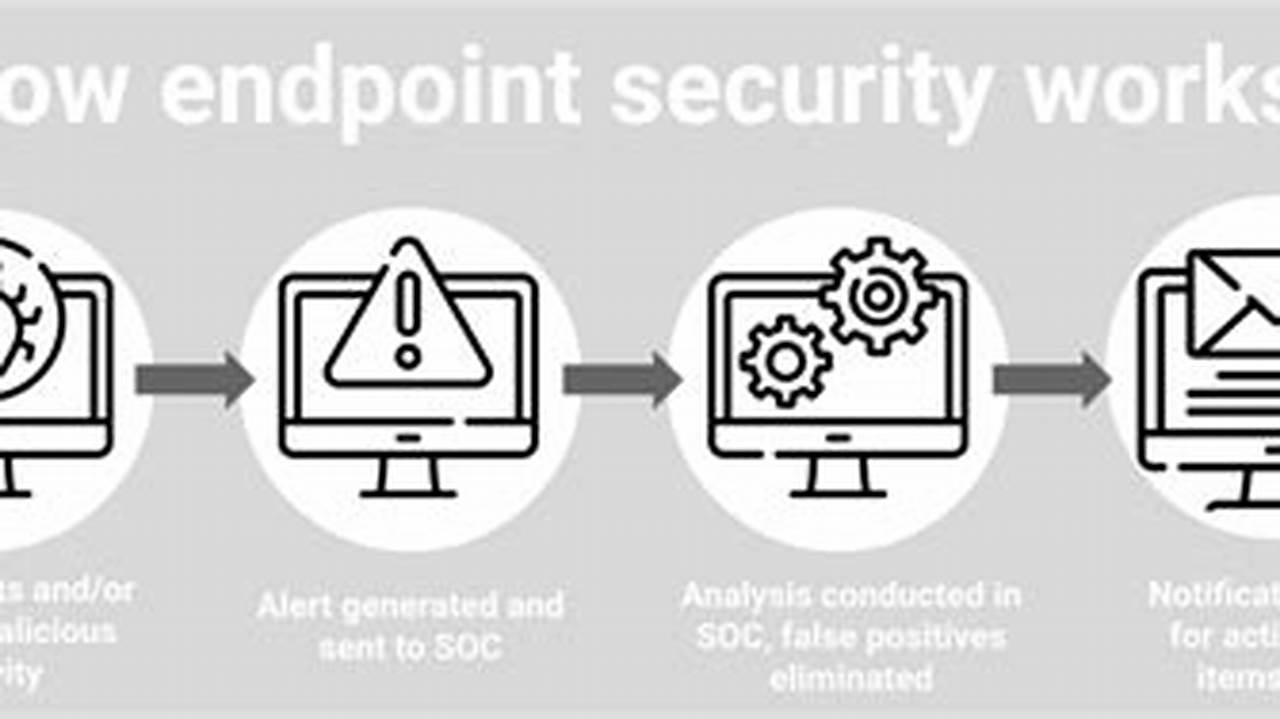
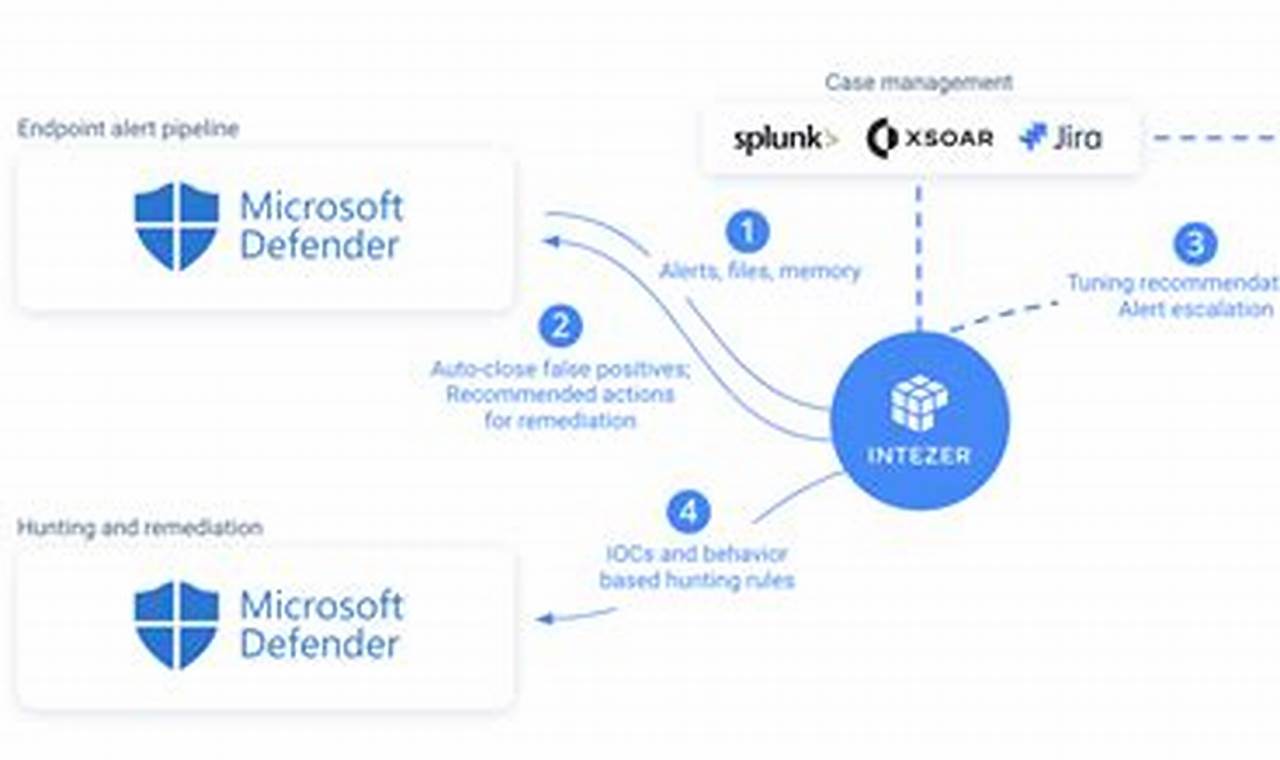
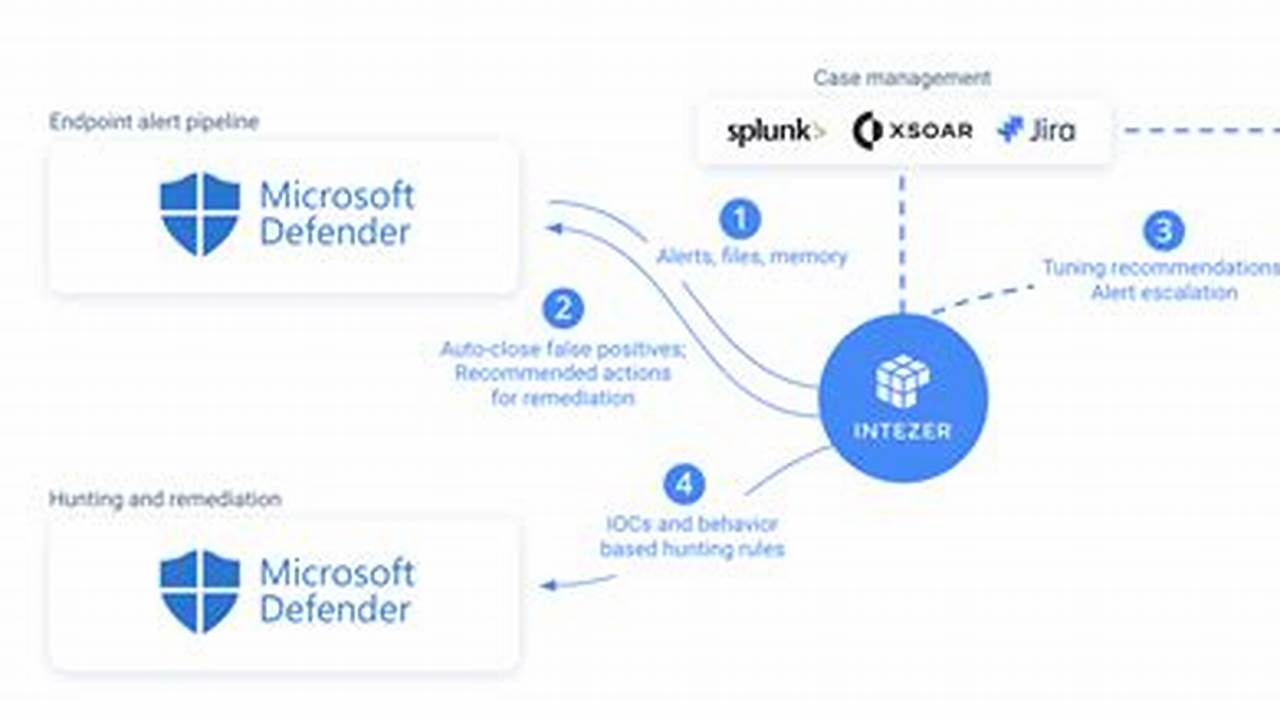
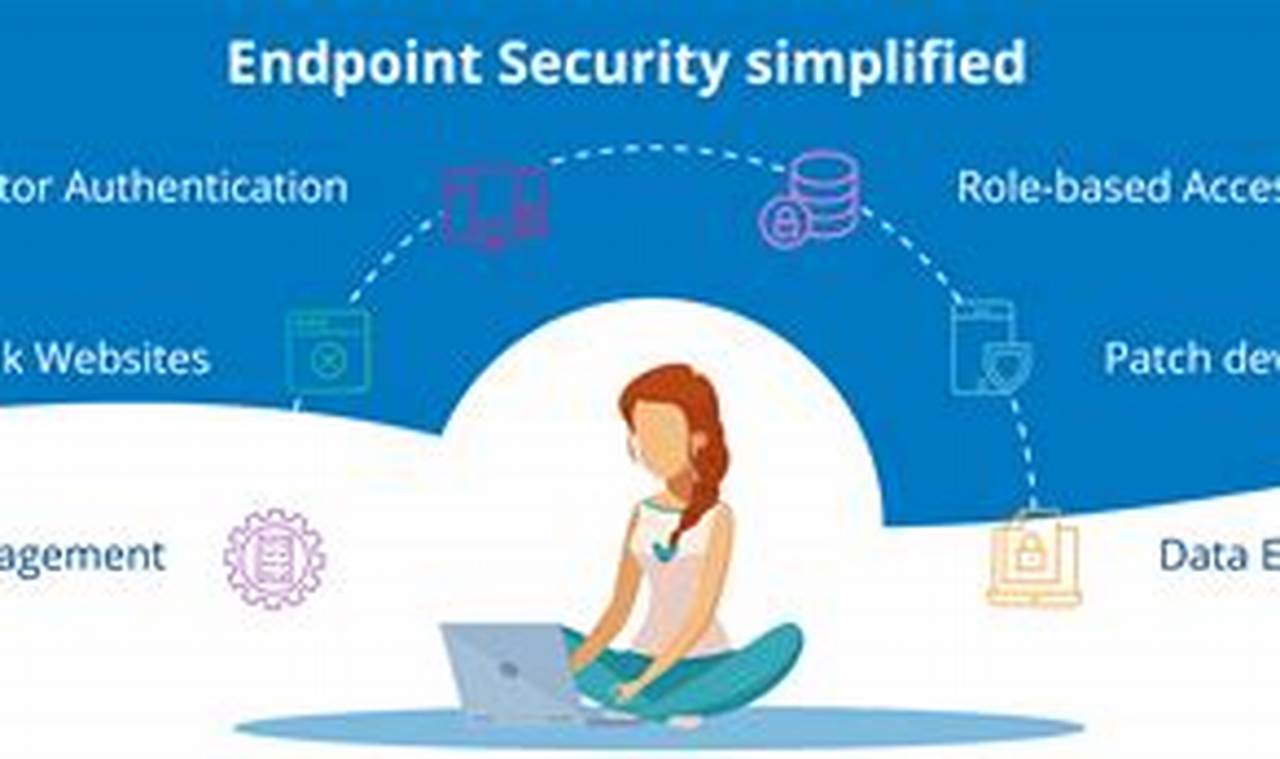
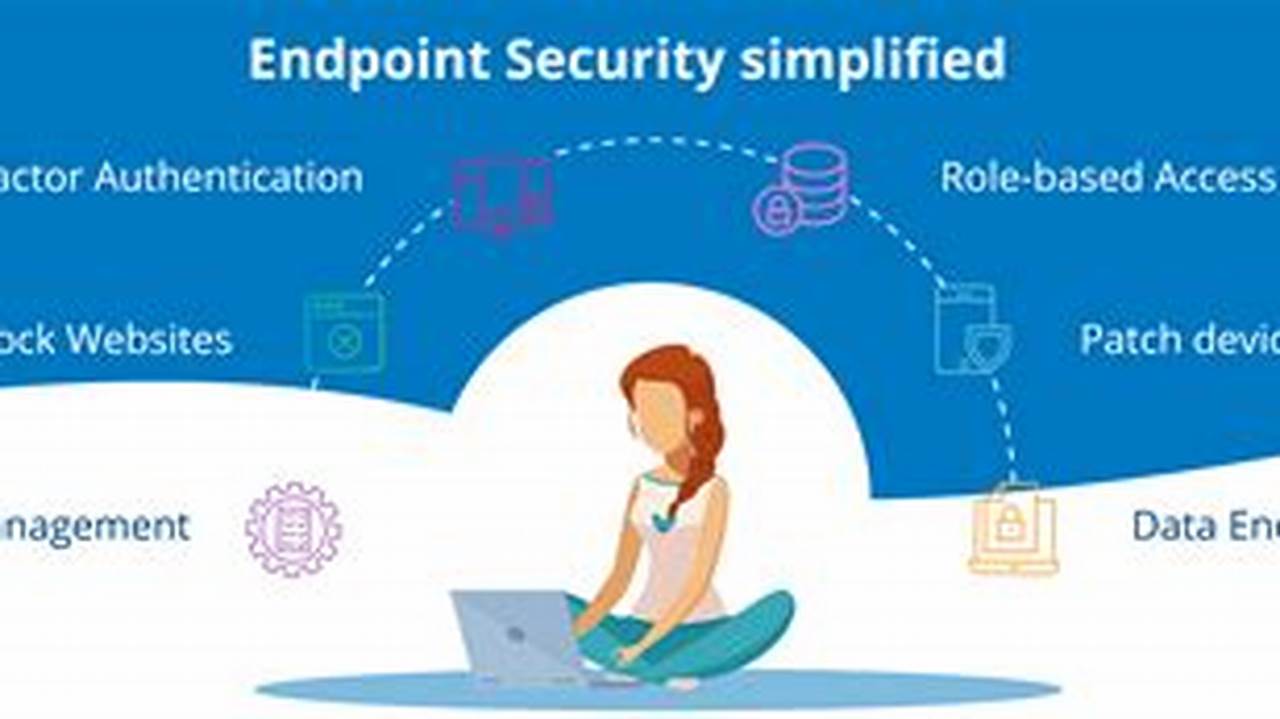
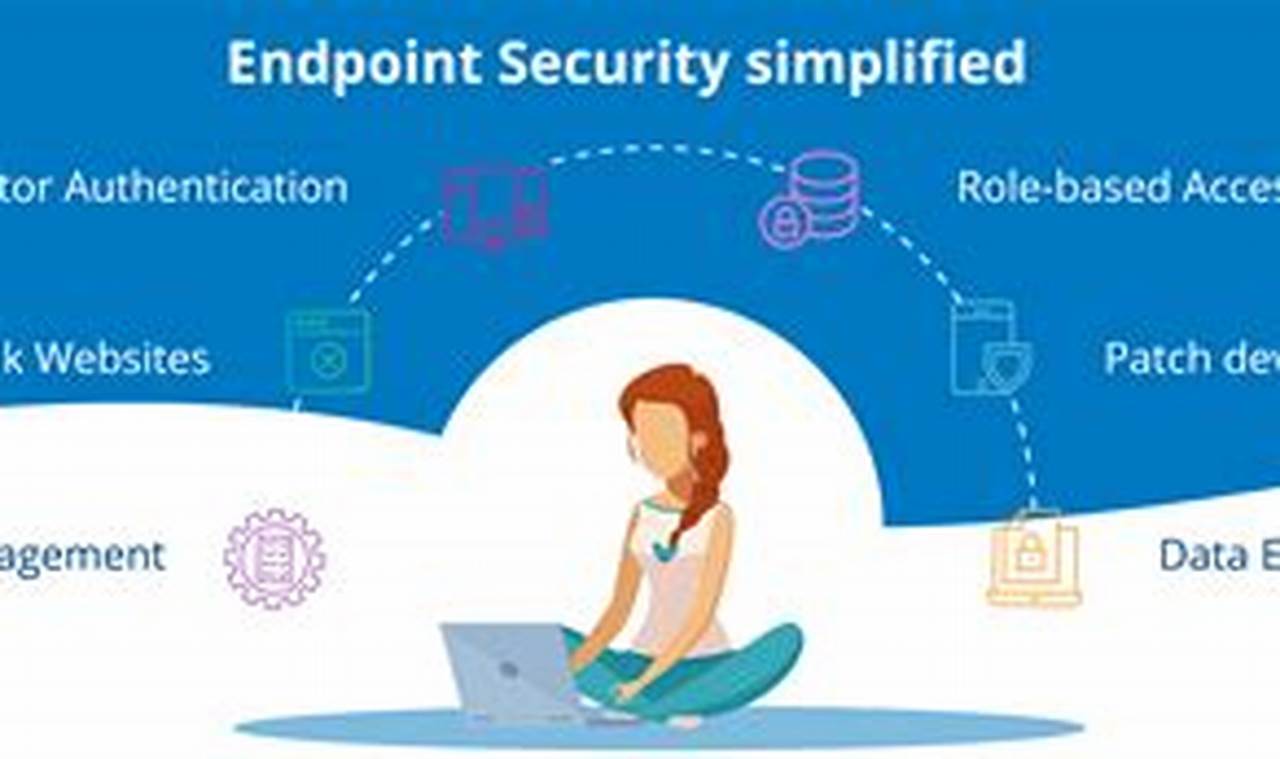
Endpoint threat detection is a crucial aspect of cybersecurity that involves identifying and responding to threats targeting endpoints, such as computers, laptops, and mobile devices. It plays a vital role in protecting sensitive data, ensuring network security, and maintaining business continuity.
Endpoint threat detection systems utilize advanced technologies to monitor and analyze endpoint activity, detecting suspicious behavior and potential threats. These systems employ various techniques, including signature-based detection, anomaly detection, and behavioral analysis, to identify and mitigate threats in real-time. Implementing endpoint threat detection significantly enhances an organization’s ability to protect against malware, ransomware, phishing attacks, and other cyber threats.