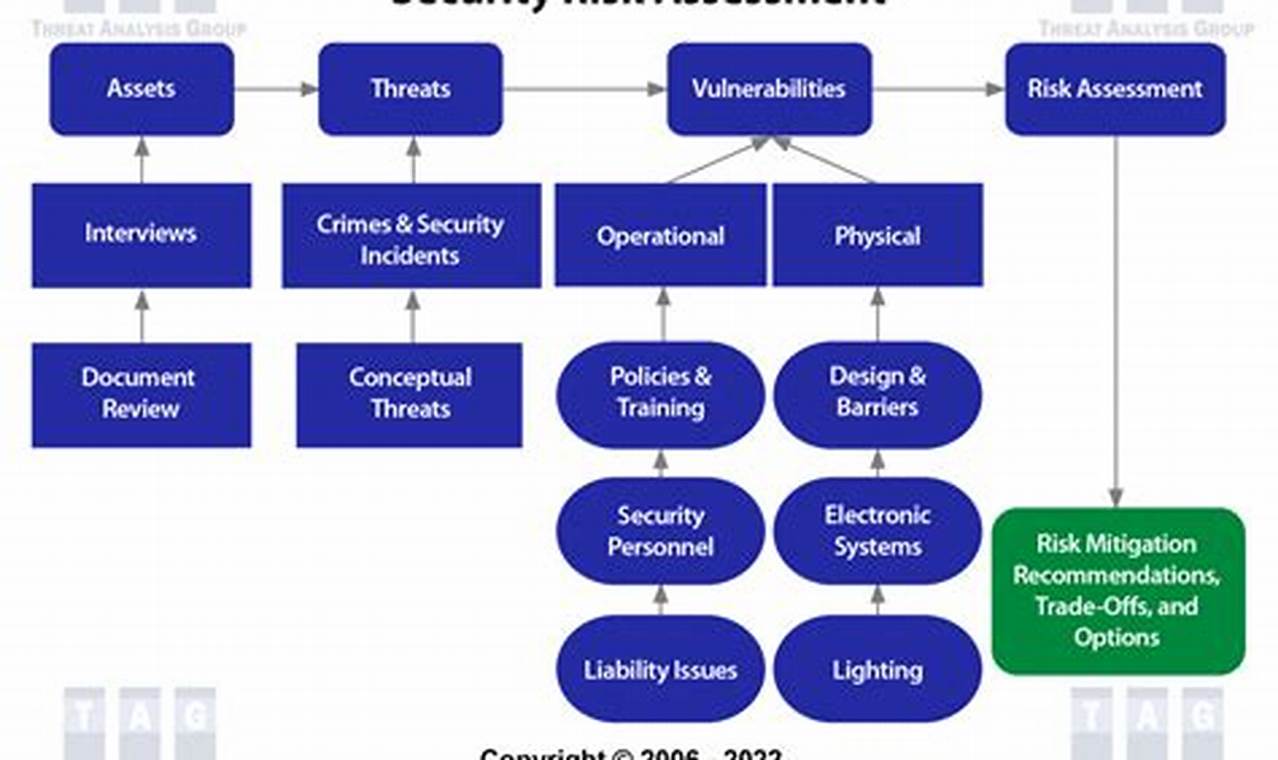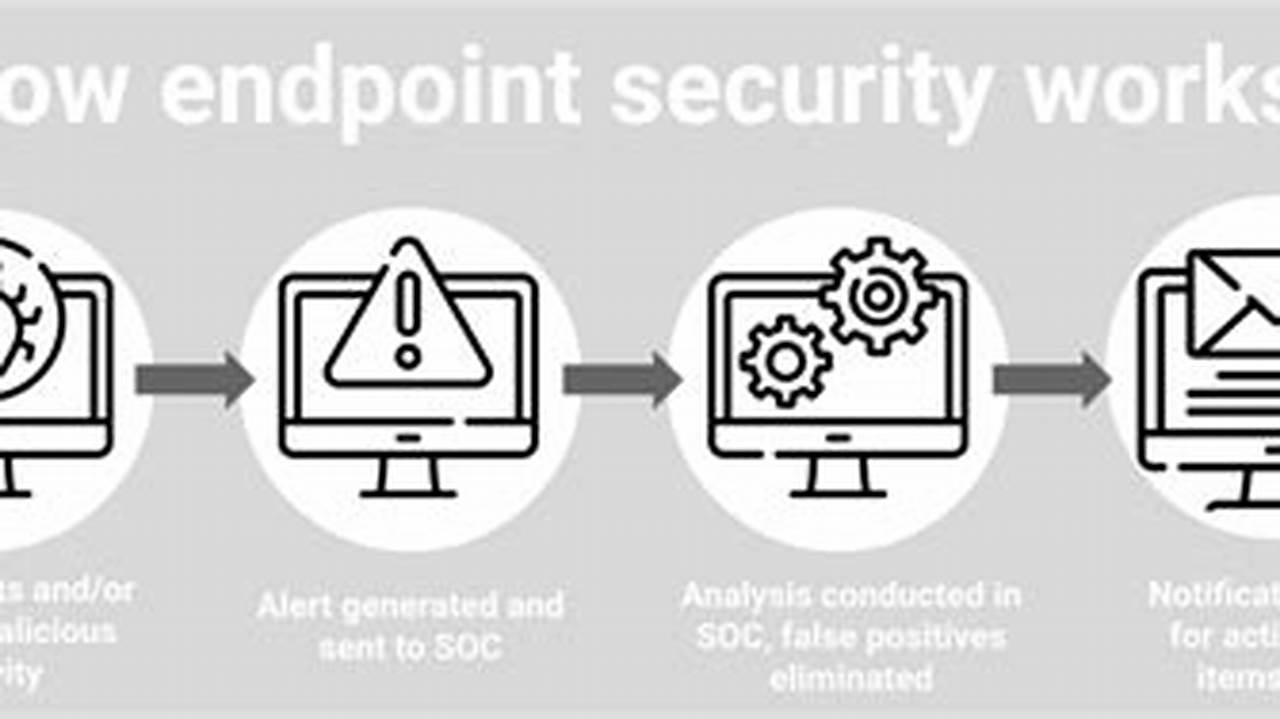
Endpoint risk management refers to the strategies and practices employed to identify, assess, mitigate, and monitor risks associated with endpointdevices. Endpoint devices are any devices that connect to a network, such as laptops, desktops, smartphones, and Internet of Things (IoT) devices. Endpoint risk management aims to protect these devices from unauthorized access, data breaches, malware infections, and other threats.
Effective endpoint risk management is crucial for organizations of all sizes. By implementing robust endpoint security measures, organizations can safeguard sensitive data, maintain regulatory compliance, and minimize the impact of cyberattacks. Endpoint risk management involves implementing security controls such as firewalls, intrusion detection systems, antivirus software, and endpoint detection and response (EDR) tools. It also includes regular security updates, employee training, and vulnerability management.